


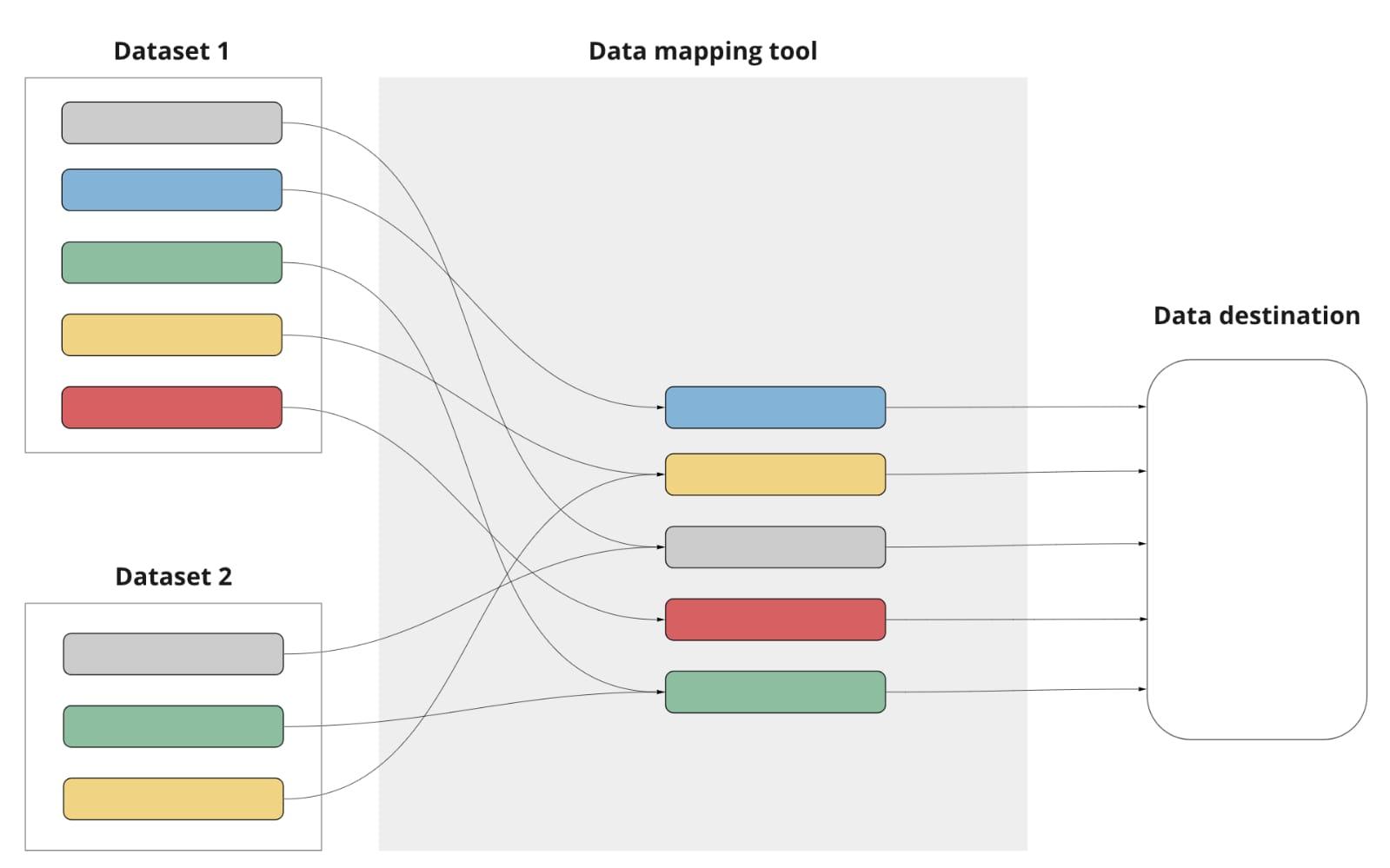
Data Mapping
1. Introduction
Data Mapping ek aisa process hai jisme hum data ko ek source se doosre source ke sath align karte hain. Jaise ki ek system ya database se doosre mein data ko correctly transfer karna. Iska main purpose data ko transform karna ya integrate karna hota hai.
2. Data Mapping kya hai?
Data Mapping ka matlab hota hai ek source data field ko destination data field ke sath match karna. Yeh ek tarika hai jisme hum ensure karte hain ki data sahi field mein jaaye aur accurately process ho.
3. Types of Data Mapping
- Manual Mapping: Isme human intervention hoti hai, jaha manually data ko map karte hain.
- Automated Mapping: Yeh software tools ka use karke kiya jata hai, jisme automatic data field mapping hoti hai.
4. Importance of Data Mapping
- Data Accuracy: Data Mapping ke bina, data galat field mein jaa sakta hai, jo analysis ko inaccurate bana deta hai.
- Data Integration: Jab hum alag-alag systems ko integrate karte hain, to data mapping ki zarurat hoti hai taaki data seamlessly flow ho.
- Data Migration: Agar hum ek purane system se naye system mein data transfer kar rahe hain, to mapping ensure karta hai ki data accurately transfer ho.
5. Data Mapping Process
- Identify the Source and Destination: Sabse pehle source aur destination data ko identify karte hain.
- Field Mapping: Phir source field ko destination field ke sath map karte hain. Jaise ki "CustomerName" ko "ClientName" ke sath match karna.
- Transformation Rules: Agar data ko kisi transformation ki zarurat ho, jaise format conversion, to yeh step mein kiya jata hai.
- Validation: Finally, map ki gayi data ko validate karte hain taaki ensure ho ki sab kuch sahi hai.
6. Applications of Data Mapping
- ETL (Extract, Transform, Load): Data Mapping kaafi zaruri hota hai jab hum data ko ek source se extract karke usko transform karke doosre system mein load karte hain.
- Data Warehousing: Data Mapping ko use karke alag-alag sources se data warehouse mein data integrate karte hain.
- Business Intelligence (BI): Accurate Data Mapping se reports aur dashboards ka data sahi hota hai, jo business decision making mein help karta hai.
7. Tools for Data Mapping
- Talend: Yeh ek popular tool hai jo data mapping ke liye use hota hai, aur isme automated features bhi hote hain.
- Informatica: Data integration aur mapping ke liye kaafi powerful tool hai.
- Microsoft SQL Server Integration Services (SSIS): Yeh data transformation aur mapping ke liye ek common tool hai.
8. Challenges in Data Mapping
- Complex Data Structures: Kabhi kabhi data structures kaafi complex hote hain, jisko map karna mushkil hota hai.
- Data Inconsistency: Agar source aur destination mein data types consistent nahi hain, to mapping kaafi challenging ho jata hai.
- Time-Consuming: Manual data mapping kaafi time le sakta hai agar data volume bahut zyada ho.
9. Best Practices in Data Mapping
- Consistent Data Types Use Kare: Hamesha source aur destination ke beech consistent data types ka use karein.
- Documentation: Sabse important step hai ki aapki mapping process documented ho taaki future mein changes ya audits ke time helpful ho.
- Testing: Har data mapping project ke baad testing karna zaruri hai taaki errors ko catch kiya ja sake.
10. Conclusion
Data Mapping data science aur IT projects mein ek essential step hai. Yeh ensure karta hai ki data sahi field mein jaaye aur accurately processed ho. Accurate mapping se hum data ko efficiently transform kar sakte hain aur apne data-driven decisions ko aur reliable bana sakte hain.