


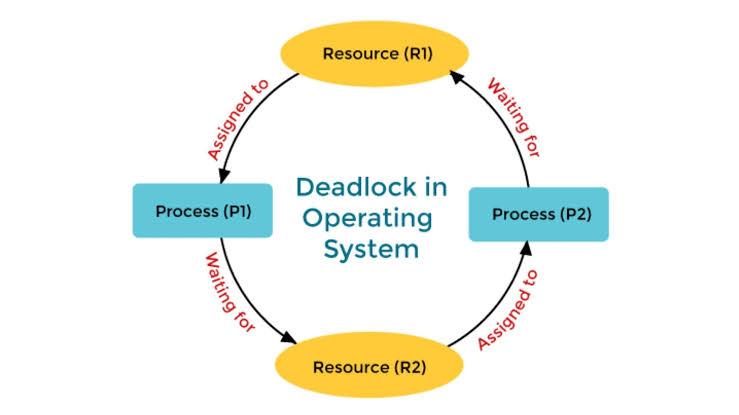
A deadlock in an operating system occurs when a set of processes become stuck in a state where each process is waiting for a resource that another process in the set is holding. As a result, none of the processes can proceed, and they all remain in a state of perpetual waiting.
Deadlock Recovery:
When a deadlock occurs, the system must recover from it to ensure that the processes can eventually complete. There are several methods for deadlock recovery:
1. Process Termination:
- Abort All Deadlocked Processes: The simplest solution is to terminate all the processes involved in the deadlock. This guarantees recovery but can result in significant work being lost.
- Abort One Process at a Time: A more refined approach is to abort processes one by one until the deadlock is resolved. The choice of which process to terminate can be based on factors such as the process's priority, the amount of work it has done, or the resources it holds.
2. Resource Preemption:
- Preempt Resources: Temporarily take resources away from some processes and give them to others. This can break the circular wait condition.
- Rollback: Roll back one or more processes to an earlier safe state and restart them, allowing the system to avoid deadlock. This method requires the system to maintain sufficient information about the states of processes.
3. Process Migration:
- Move Processes to Different Systems: In distributed systems, processes can be moved to other systems where the required resources are available. This approach can help avoid deadlock but requires advanced system capabilities.
4. Combination Methods:
- Sometimes, a combination of process termination and resource preemption might be used to resolve deadlocks more effectively.
The choice of deadlock recovery method depends on the specific system and the criticality of the processes involved.