


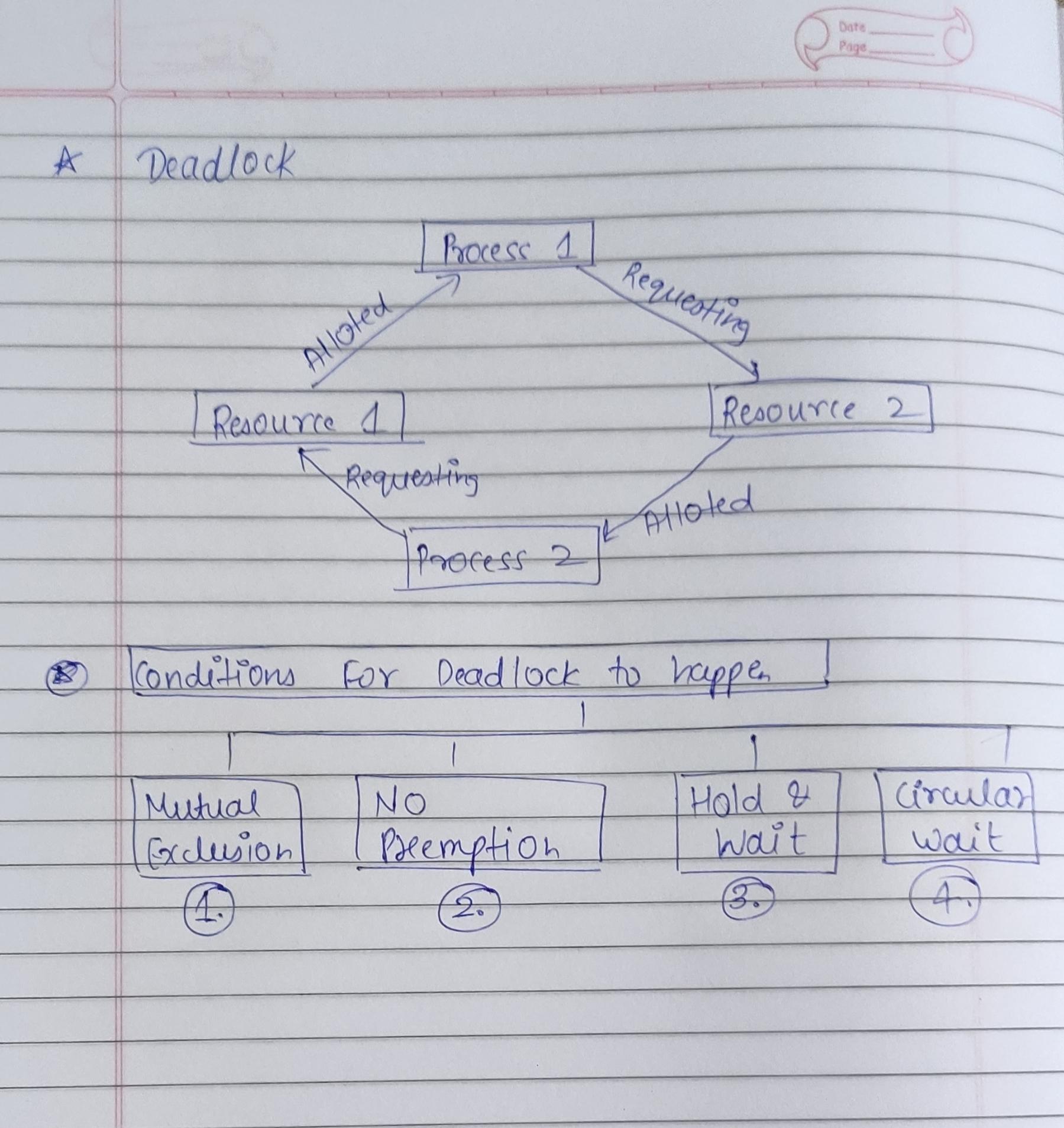
Let's first understand what is deadlock, Deadlock is the situation where two or more processes are waiting for some process or event to happen but that event will never happen. It is kind of situation where a set of processes are blocked because each process is holding a resource and waiting for another resource acquired by some other process.
Example, There is two process namely P1 and P2 holding some resource like R1 and R2 respectively, P1 is saying that I need R2 to proceed and P2 is saying I need R1 to proceed but non of them will release that particular resource, so in case both process are waiting for some event to get happen but that event will never happen. Ultimately this situation refer to the concept of Deadlock.
Now let's understand some conditions that should be met for happening of Deadlock, there is Four necessary condition that should be met for Deadlock happening, that are as follows.
1. Mutual Exclusion:- It is situation where two processes cannot use same resources at same time. The process is in the critical section where it is using the resource and at the same time some other process comes in for that resource. Critical Section refers to the situation where the process will use the resource until it gets over and none of other process will not access that resource until the critical section process gets over.
2. Hold and Wait:- This refer to A process holding a resource and waiting for another resource at same time. There is also a situation where another process who was holding a resource and waiting for a resource that is acquired by some other resources.
3. No preemption:- The process which once scheduled will be executed till the completion. It is kind of situation where if one process is using some resource and some other process is saying that I want this resource irrespective of the high preference that resource should not be released until the process is completed. There should be equal priority given to each process.
4. Circular Wait:- This refer to the situation where all the processes are waiting for the resource in a cyclic manner. This is kind of looping where each processes is waiting for some resource to get proceed but that resource is acquired by some processes, there can be many processes also.
So with this information we learned about Deadlock and 4 necessary condition that should be satisfied then there is a Deadlock situation.