


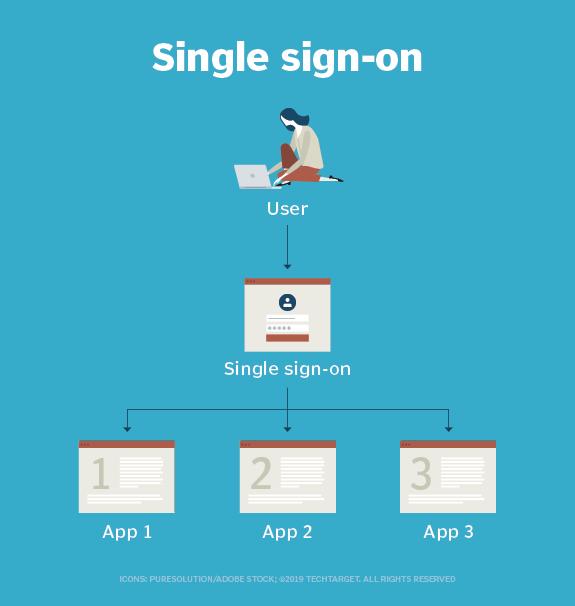
Single sign-on (SSO) is a session and user authentication service that permits a user to use one set of login credentials -- for example, a username and password -- to access multiple applications. SSO can be used by enterprises, small and midsize organizations, and individuals to ease the management of multiple credentials.
Single sign-on is a federated identity management arrangement. The use of such a system is sometimes called identity federation. Open Authorization (OAuth) is the framework that enables an end user's account information to be used by third-party services, such as Facebook, without exposing the user's password.
OAuth acts as an intermediary on behalf of the end user by providing the service with an access token that authorizes specific account information to be shared. When a user attempts to access an application from the service provider, the service provider sends a request to the identity provider for authentication. The service provider then verifies the authentication and logs the user in.
In a basic web SSO service, an agent module on the application server retrieves the specific authentication credentials for an individual user from a dedicated SSO policy server, while authenticating the user against a user repository, such as a Lightweight Directory Access Protocol directory. The service authenticates the end user for all the applications the user has been given rights to and eliminates future password prompts for individual applications during the same session.
Some SSO services use protocols, such as Kerberos or Security Assertion Markup Language (SAML):