


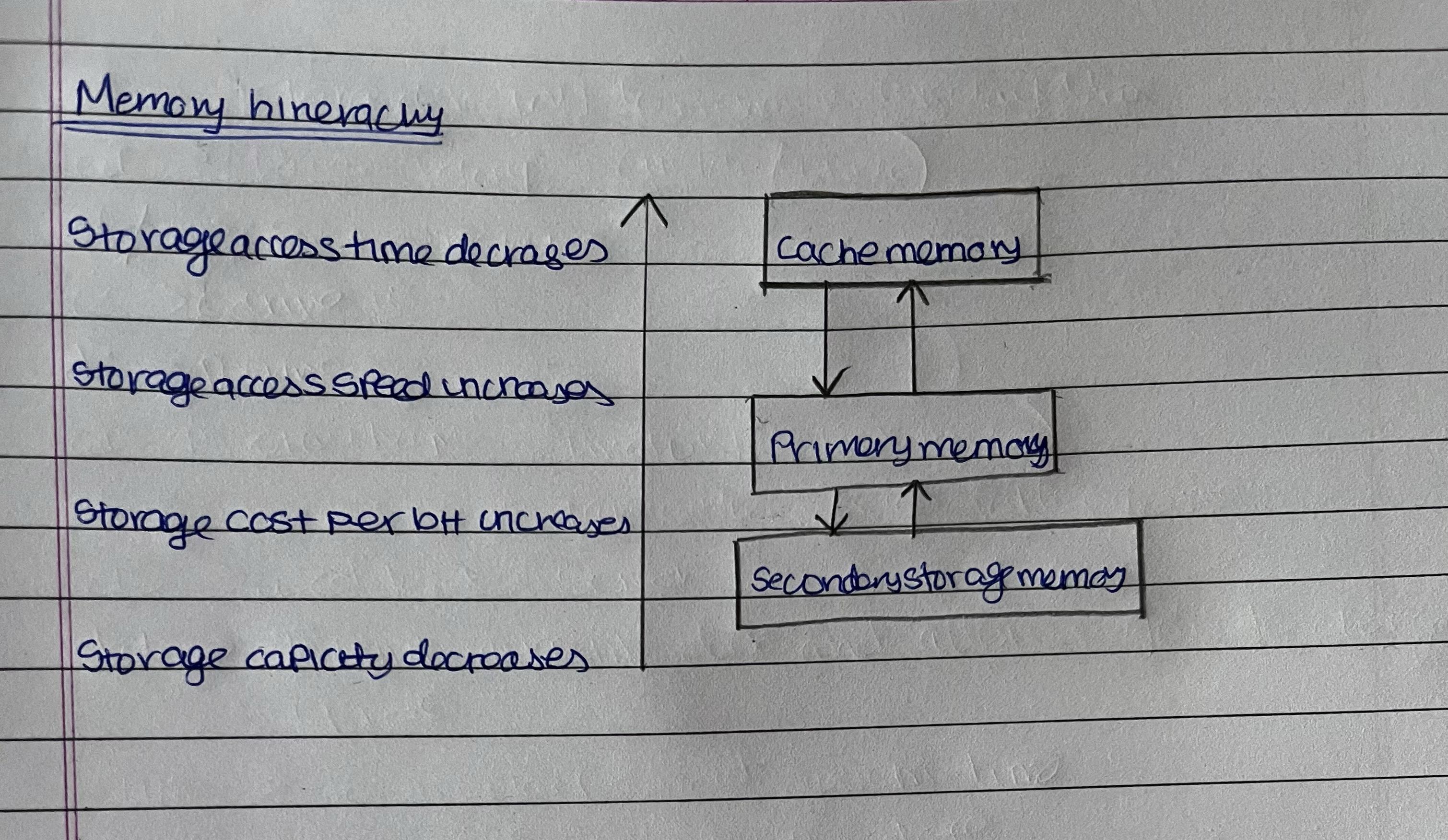
During the design of computer memory you should consider the speed of the memory , capacity of the memory and the cost of the memory . Greater capacity generally means slower access speed and lower cost per bit.Faster access time usually means higher cost per bit and lower capacity.There is a tradeoff between them to balance the trade off computer uses memory hierarchy . There are three types of memories cache memory , primary (main ) memory and secondary storage memory . Primary memory stores currently needed program instructions and data only. Secondary memory stores data and program which are not actively needed . Cache memory is extremely high speed compared to other and is present in processor . Cache memory is used to store data which has to executed . A processor may access the program and data from the main memory and cache memory . The computer system should move data and programs from secondary memory to primary memory before the processor can refer them and only the current instruction to be executed is stored in cache memory . The result is stored in primary memory and it will send executed data to secondary storage .
In the memory hierarchy while going from down to up the storage access time decreases the speed increases, cost per bit increases and storage capacity decreases . Secondary storage memory has large storage capacity, primary memory has small capacity and cache memory has least storage capacity.
Secondary storage contains complete folder which will be transferred to primary memory ,only the currently executed file will be transferred to cache memory and the executed data will be moved to the register and cpu will execute the operation . Again the process will continue like this .
memory design is about balancing capacity, access speed, and cost through a hierarchy of memory types, ensuring that the system performs efficiently without excessive cost.
~khushi sanghavi
ASSIGNMENT 1 (53003230009)