


o virtual memory technique. Virtaul memroy creates an illusion of larger memory space than physically available by utilizing secondary storage (hard drive) for extending RAM. It does it by swapping temporarily less used parts of programs to virtual memory freeing up the space of RAM for current use. This allows the system to multitask more effectively by exceeding the physical memory RAM capacity.
Protection: The OS enforces a strict hierarchy of memory access permissions. The kernel, the core of the operating system, enjoys the highest privilege level and has unrestricted access to all memory regions. User processes, on the other hand, operate with limited privileges. They can only access memory locations explicitly allocated to them and are prohibited from modifying critical system areas.
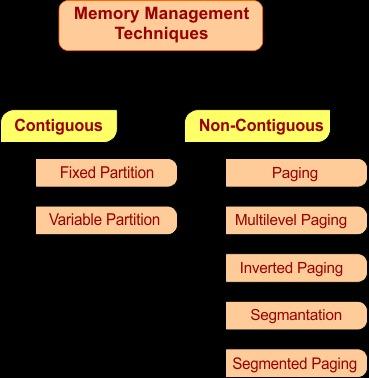
Techniques of Memory Management :
Contiguous Memory Allocation : In contiguous memory allocation elements are allocated in continous order i.e. a single contiguous block of memory. This means all memroy is assigned to a process are in a continous range. In Programming array is a good example of this in array elements are stored in contiguous (conitnous) format. As it is contiguous it is easy to implement and calculating address is simple as compared to non contiguous. As all memory is contiguous accessing memory is fast. But as it is contiguous it is hard to allocate memory i.e. it is hard to find free conotiguous memory space. And it is also not flexible as if there is somthing stored next to that contiguous memory it will be hard to extend it.
Non Contiguous Memory Allocation : In non contiguous memory allocation every element is stored in different locations (memory is not next to it like in contiguous memory allocation) blocks can be placed anywhere in physical memory. As memory is non contiguous memory is efficiently utilized and is also flexible as elements are stored in different locations. Memory isolation is easier to implement as every memroy is at different locations so it will be hard to access the memory that increases the security. But there are some limitations too like it increases the complexity and also calculation of address is difficult as compared to contiguous memory allocation.