


TOPIC : MEMORY MANAGEMENT
As the word itself states, we are talking about managing the memory on the computer logically and not physically.
In the context of OS, the operating system involves the process of managing computer memory by making various decisions and concepts.
The below key points highlight the memory management process, benefits and usages.
• Allocation & Deallocation: The OS has the role of allocating memory as per requirement and whenever not required the memory should be free or should get deallocated. So that the usage of storage resources are done at maximum level ( pura ache se memory use hoga without wastage of storage).
• Memory Protection: The allocated memory is protected and would not be allocated(kisi aur user ko wohi memory allocate nahi hogi) to any other user until the user wishes to overwrite the memory. As well as it also take care of that data( leak nahi hota).
• Process Isolation: mein sab process independent hoti hai taaki koi ek bhi fail ho toh dusre par affect naa ho aur sab continuous manner mein kaam chalta rahe.
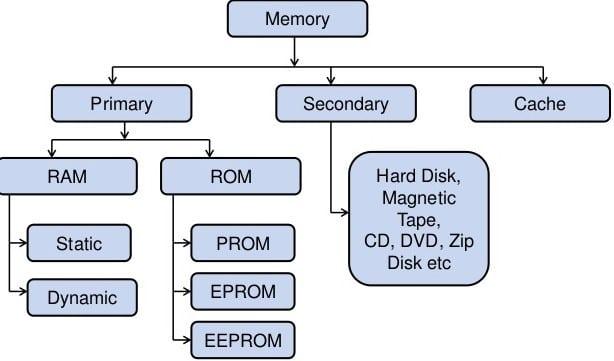
•Cache Management: Operating system cache memory ko manage karne ka kaam karta hai jisse ki, kaam karne ki speed badh jaati hai, aur current access data store ho sake jo background mein use ho rha hoga.
Effective memory management bohot helpful better speednof execution and best use of storage resources ke liye!
The below example of running multiple applications at same time helps to explain the concept of memory management:
Imagine ke hamare pass 4gb ram ka computer aur ham ek sath background mein bohot sara apps chala rahe hai.
-Typing words document
-Playing music
-Web browser for searching information
Etc.. simultaneously chal raha hai