


What is Memory Management?
In a multiprogramming computer, the Operating System resides in a part of memory, and the rest is used by multiple processes. The task of subdividing the memory among different processes is called Memory Management. Memory management is a method in the operating system to manage operations between main memory and disk during process execution. The main aim of memory management is to achieve efficient utilization of memory. In Simpler words, Memory management is the process of controlling and coordinating a computer's main memory. It ensures that memory space are properly managed and allocated so the operating system (OS), applications and other running processes have the memory they need to carry out their operations. So the functions of each process will happen smoothly.
Why memory management is Required?
1.Allocate and de-allocate memory before and after process execution.
2.To keep track of used memory space by processes.
3.To minimize fragmentation issues.
4.To proper utilization of main memory.
5.To maintain data integrity while executing of process.
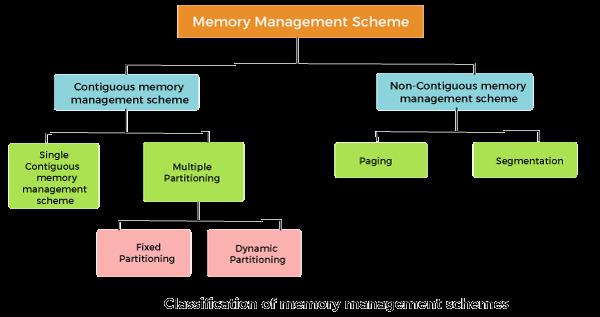
The memory management techniques can be classified into following:
Contiguous memory management schemes and Non-Contiguous memory management schemes, this is explained further below,
1.Contiguous Memory Management Schemes:-
Contiguous memory management is a way to allocate memory for programs in a computer.
Let's understand with an example here,
Imagine you have a big library with many books (programs) that need to be stored on shelves (memory). Contiguous memory management assigns each book in a continuous block of shelves, so all the pages (data) of a book are together in one place.
It is discussed below how it will work:
1.Fixed-size partitions: Divide the library (memory) into fixed-size sections (partitions) like small, medium, and large shelves.
2.Program allocation: When a program (book) needs memory, find a partition that fits its size and allocate it.
3.Continuous block: Assign a continuous block of shelves within the partition to the program, so all its data is stored together.
2.Non-Contiguous memory management schemes:-
Non-Contiguous memory management is a way to allocate memory for programs in a computer, where programs don't need to be stored in a single, continuous block of memory. Here's a simplified explanation:
Let's take the same example from above to understand and relate with it, Non-Contiguous memory management allows books to be stored in different sections of the library, as long as there's enough space.
Let's understand how it will works:-
1.Paging: Divide the library (memory) into small, equal-sized sections called pages.
2.Program allocation: When a program (book) needs memory, allocate pages from anywhere in the library.
3.Page table: Keep a page table (index) to track which pages belong to which program.