


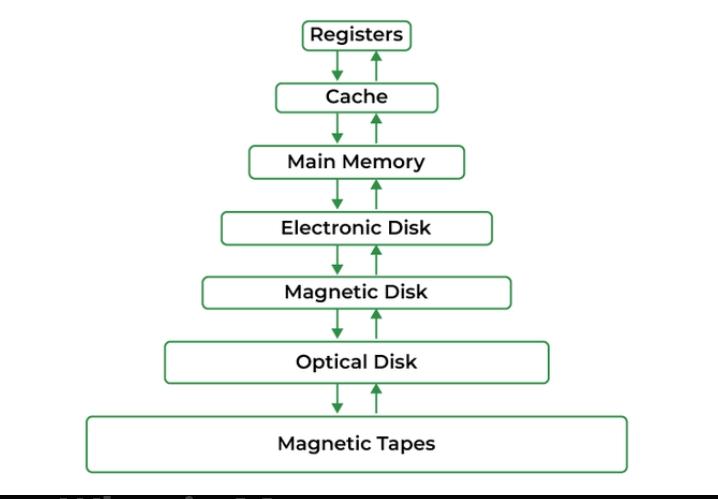
Memory Management
Memory management is an OS function that handles the allocation and deallocation of memory resources for processes, ensuring efficient and secure use of the system's memory.
1. Frames: Fixed-sized blocks of physical memory. The OS divides memory into frames for easier management.
2. Page: Fixed-sized blocks of logical memory in a program. Pages are mapped to frames in physical memory.
3.segment: Variable-sized blocks of memory representing logical units like functions or data structures. Segments allow more flexible memory allocation.
Memory Management Requirements
- Relocation: Allows processes to be moved in memory, enabling efficient use of available space.
- Protection: Ensures that processes do not interfere with each other’s memory, maintaining system stability and security.
- Sharing: Enables multiple processes to share memory, such as libraries, while maintaining protection.
- Logical Organization: Organizes memory into segments or pages, reflecting the logical structure of programs.
- Physical Organization: Manages the mapping of logical memory to physical memory, optimizing performance and resource use.