


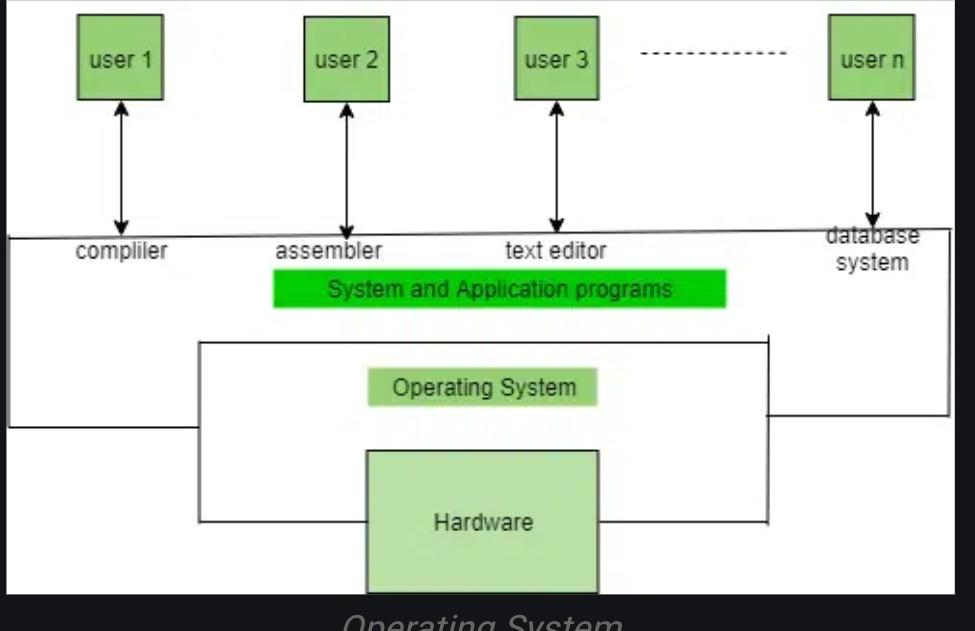
An Operating System (OS) performs several functions to manage computer hardware resources and provide common services to computer programs.
The main functions of an OS can be categorized into the following:
1. Process Management:
• Process creation and termination
• Process scheduling (allocating CPU time to processes)
• Process synchronization (managing access to shared resources)
• Process communication (inter-process communication)
2. Memory Management:
• Memory allocation and deallocation
• Memory protection (preventing unauthorized access)
• Memory mapping (translating logical addresses to physical addresses)
• Virtual memory management (using disk storage to supplement RAM)
3. File Management:
• File creation, deletion, and modification
• File organization (directories, folders, etc.)
• File access control (permissions, access rights)
• File storage and retrieval
4. Input/Output (I/O) Management:
• Managing input/output operations between devices and programs
• Providing interfaces for devices (e.g., keyboard, mouse, display)
• Managing I/O requests and scheduling
5. Security:
• User authentication and authorization
• Access control (permissions, access rights)
• Encryption and decryption
• Intrusion detection and prevention
6. Interrupt Handling:
• Handling interrupts generated by hardware devices
• Context switching (switching between processes)
• Interrupt-driven I/O