


Paging in Operating Systems
Paging is a memory management scheme used by operating systems to eliminate the problem of fitting varying-sized processes into fixed-sized memory spaces. It allows a process's physical memory to be non-contiguous, effectively avoiding fragmentation and ensuring efficient use of memory.
How Paging Works :
Logical and Physical Memory Separation :
Paging separates the logical address space (the addresses used by programs) from the physical address space (the actual addresses in RAM). This means a program’s memory can be scattered across different locations in physical memory, while still appearing contiguous to the program itself.
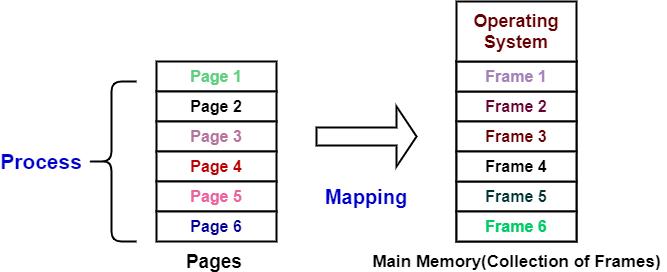
Pages and Frames
Pages: The process’s logical memory is divided into fixed-sized blocks called pages.
Frames: The physical memory is also divided into blocks of the same size as the pages, called frames.
The OS loads pages from the logical address space into available frames in the physical address space.
Page Table
The operating system maintains a page table for each process. This table maps the logical pages to their corresponding frames in physical memory. When a program references a memory address, the CPU uses the page table to translate the logical address into a physical address.
Address Translation
Every memory access by a program involves two components: the page number and the page offset.
The page number identifies the specific page in the page table.
The page offset is the exact location within the page.
The operating system uses this information to find the corresponding physical address in the frame.