Privacy-Enhancing Computation Techniques refer to a set of advanced methods and technologies that enable data analysis, processing, and collaboration while preserving the privacy of sensitive information. These techniques are crucial in situations where individuals, organizations, or entities need to work with data without directly exposing its content. The primary objective is to strike a balance between deriving valuable insights from data and safeguarding individual privacy rights.
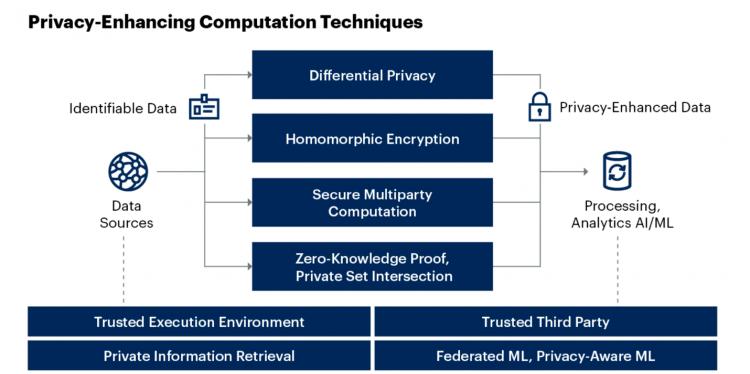
- The article covers the following key techniques:-
- Homomorphic Encryption: In simple terms the use of homomorphic encrption to be keep data confidential through algorithms transformation. This technique allows computations to be performed on encrypted data, preserving its privacy throughout the analysis process. We explore both partially homomorphic and fully homomorphic encryption methods, showcasing their role in secure data processing.
- Secure Multi-Party Computation (SMPC): SMPC enables multiple parties to collaboratively compute results without revealing their individual data. By detailing how parties can jointly analyze data without exposing it, we highlight the importance of secure collaboration.
- Differential Privacy: Differential privacy involves injecting controlled noise into data to protect individual privacy while maintaining accurate analyses. We explain how this technique maintains a delicate balance between data utility and privacy.
- Zero-Knowledge Proofs: Zero-knowledge proofs allow the verification of information without disclosing the actual data. Real-world applications demonstrate the value of proving knowledge without sharing sensitive details.
- Real-World Applications and Benefits: -The power of Privacy-Enhancing Computation Techniques is best understood through real-world applications. From healthcare providers collaborating on patient data analysis without exposing medical records to financial institutions detecting fraudulent transactions without viewing individual purchases, these techniques are reshaping industries while respecting privacy rights.
- What is privacy computing : -Privacy computing is a powerful cloud computing technology that insulates sensitive data and protects. Privacy computing networks are virtually invisible and aren’t able to be tracked or recognized by attackers or cloud providers.Cloud data privacy is becoming more crucial than ever during the digital age, as more and more businesses automate processes and take the steps to move full force into the digital expanse. Privacy computing removes the persisting data security exposure by protecting data that is in use during processing or runtime. Privacy computing aims to provide assurances to businesses and facilitates the transfer of sensitive data to public cloud services.
- Conclusion: -In a world where data's potential seems limitless, striking the right balance between utility and privacy is a paramount concern. Privacy-enhancing computation techniques are the guiding light that navigates this intricate landscape. As we conclude this journey through the realm of encrypted calculations, secure collaborations, and data privacy safeguards.



