


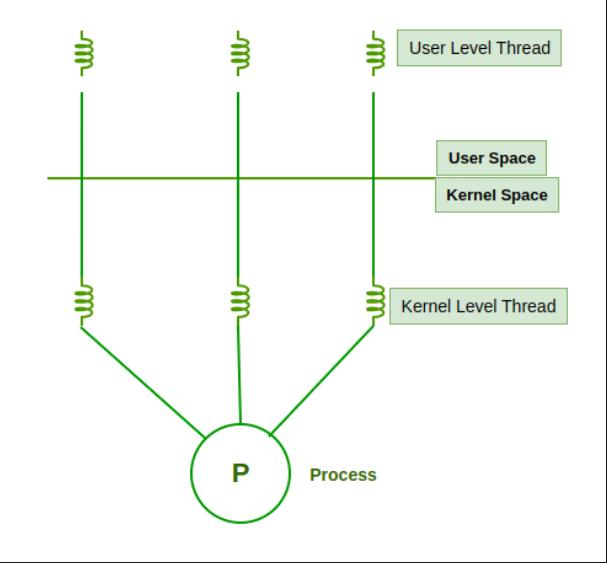
A thread is a single sequence stream within a process. Threads are also called lightweight processes as they possess some of the properties of processes.
Each thread belongs to exactly one process. In an operating system that supports multithreading, the process can consist of many threads. But threads can be effective only if the CPU is more than 1 otherwise two threads have to context switch for that single CPU.
What is Thread in Operating Systems?
In a process, a thread refers to a single sequential activity being executed. these activities are also known as thread of execution or thread control. Now, any operating system process can execute a thread. we can say, that a process can have multiple threads.
Why Do We Need Thread?
Components of Threads
These are the basic components of the Operating System.