



In the intricate world of cyber forensics, understanding email servers is paramount for investigators seeking to unveil the truth behind digital crimes. Email communication is a ubiquitous feature of modern life, making email servers a crucial component in the cyber forensic landscape. This article aims to delve into the intricate workings of email servers, exploring their significance, challenges faced by forensic investigators, and the methodologies employed to unravel digital mysteries.
Architecture of Email Servers:
Email servers play a pivotal role in facilitating electronic communication. They consist of multiple components, including Mail Transfer Agents (MTAs), Mail Delivery Agents (MDAs), and Mail User Agents (MUAs). Understanding these elements is essential for cyber forensic professionals to trace the path of digital evidence, such as malicious emails or unauthorized access.
MTAs are responsible for routing and transferring emails between servers. In a forensic context, tracing the journey of an email through various MTAs can provide insights into the origin, transmission, and potential alterations made during transit.
MDAs handle the final delivery of emails to the recipient's mailbox. Forensic investigators focus on MDAs to identify any anomalies, unauthorized access, or tampering that might have occurred during the delivery process.
MUAs are the client applications that users interact with to send and receive emails. Analyzing MUAs can provide forensic experts with information on user activities, account compromises, or any suspicious behavior related to email communication.
How does a mail server work?
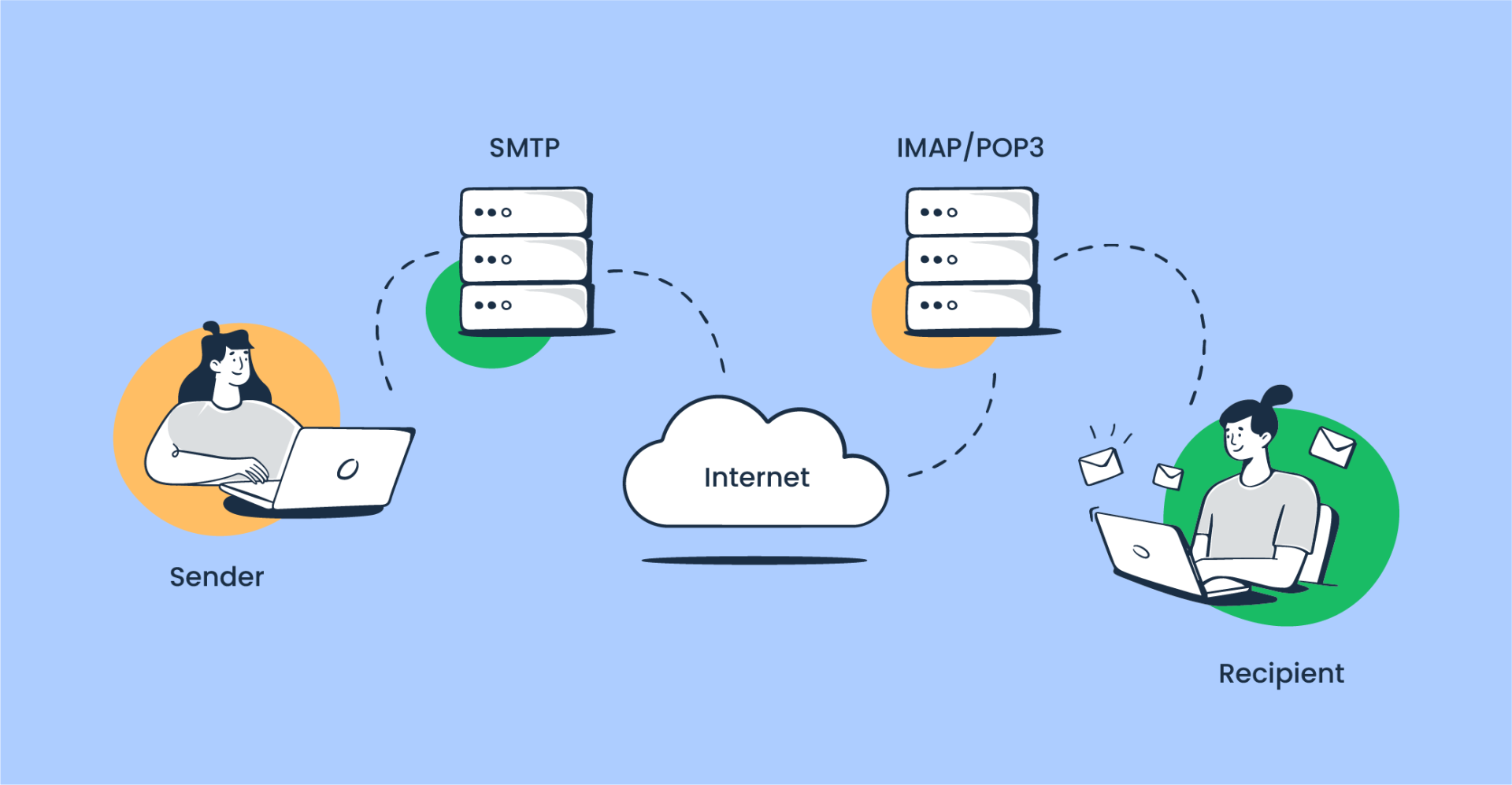
here's a step-by-step explanation of how a mail server works:
1. Sender Composes Email: The sender creates an email using an email client (such as Outlook, Gmail, Thunderbird, etc.). They enter the recipient's email address, compose the message, and may attach files or include links.
2. Sender's Email Client Contacts Outgoing Mail Server: When the sender clicks "Send," their email client contacts their outgoing mail server (also known as SMTP server). The email client communicates with the server using the SMTP protocol.
3. Authentication and Authorization: The outgoing mail server authenticates the sender's credentials to ensure they have permission to send emails through the server. This step helps prevent unauthorized users from abusing the mail server for sending spam or malicious emails.
4. Message Routing: Once authenticated, the outgoing mail server determines the recipient's mail server based on the email address domain. It looks up the recipient's domain's mail exchange (MX) records in DNS (Domain Name System) to find the address of the recipient's incoming mail server.
5. Connection Establishment: The sender's mail server establishes a connection with the recipient's mail server using the SMTP protocol. It sends a series of commands and responses to negotiate the email transmission.
6. Message Transfer: After the connection is established, the sender's mail server transfers the email message to the recipient's mail server. This transfer occurs over the internet and may involve multiple intermediate mail servers if the sender's and recipient's servers are not directly connected.
7. Recipient's Mail Server Receives Email: The recipient's mail server receives the email message from the sender's server. It stores the message temporarily in a mail queue while it performs checks and processing.
8. Spam and Virus Scanning: The recipient's mail server may perform various checks on the incoming email, including spam filtering and virus scanning, to detect and block malicious or unwanted content.
9. Delivery to Recipient's Inbox: If the email passes all checks and is not flagged as spam or containing malware, the recipient's mail server delivers the email to the recipient's inbox or designated folder.
10. Recipient Accesses Email: Finally, the recipient accesses their email using an email client (such as Outlook, Gmail, etc.) or a webmail interface provided by their email service provider. They can read, reply to, forward, or delete the received email as needed.
These steps outline the basic process involved in sending and receiving emails between mail servers. Behind the scenes, there are additional complexities and optimizations involved to ensure reliable and efficient email delivery.
Challenges in Email Server Forensics:
The prevalence of end-to-end encryption in modern email services poses challenges for forensic investigators. Privacy concerns and encrypted communication can hinder the ability to access and analyze email content during forensic examinations.
Email servers are often targeted in phishing and spoofing attacks, making it challenging for investigators to distinguish between legitimate and malicious communications. Advanced forensic techniques are required to trace the origin of deceptive emails.
The global nature of email communication introduces jurisdictional complexities for cyber forensic professionals. Investigating crimes involving email servers may require collaboration between international law enforcement agencies and adherence to various legal frameworks.
Methodologies in Email Server Forensics:
Examining server logs is a fundamental aspect of email server forensics. Logs can reveal critical information such as IP addresses, timestamps, and user activities, assisting investigators in reconstructing the sequence of events.
Metadata associated with emails, including sender and recipient details, timestamps, and routing information, offers valuable insights for forensic examinations. Analyzing metadata aids in establishing the authenticity of email communications.
Understanding the network infrastructure connecting email servers is crucial. Network forensics helps investigators trace the communication flow, detect anomalies, and identify potential security breaches.
In the ever-evolving landscape of cyber forensics, comprehending the intricacies of email servers is indispensable for investigators seeking to uncover digital evidence. The challenges posed by encryption, phishing, and jurisdictional complexities necessitate advanced methodologies and collaboration across borders. As technology continues to advance, so too must the skills and techniques employed by cyber forensic professionals to navigate the complex web of email server investigations.
References:
1] Axigen (2021). What Is an Email Server? Definition, How It Works, Why You Need One? | Axigen. [online] www.axigen.com. Available at: https://www.axigen.com/articles/what-is-an-email-server_107.html
2] Anfalovas, I. (2022). What Is an Email Server? How Does It Work? [online] IPXO. Available at: https://www.ipxo.com/blog/what-is-an-email-server/
3] resources.infosecinstitute.com. Email analysis Infosec. [online]. Available at: https://resources.infosecinstitute.com/topics/digital-forensics/email-analysis/
4] What is Mail Server?. Available at: https://www.cloudflare.com/learning/email-security/what-is-a-mail-server/
5] mailtrap.io. (2022). Email Infrastructure: The Definitive Guide [2023]. [online] Available at: https://mailtrap.io/blog/email-infrastructure/