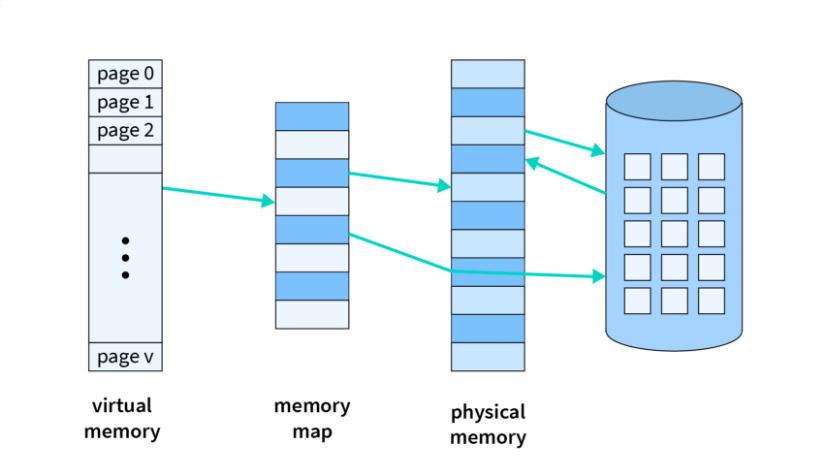
Virtual memory is a fundamental concept in operating systems (OS) that allows a computer to compensate for shortages of physical memory by temporarily transferring data from random access memory (RAM) to disk storage. This process creates an "illusion" for users that there is more memory available than what is physically present on the system.
Key Concepts of Virtual Memory:
- Paging:
- The OS divides both the physical memory (RAM) and virtual memory into fixed-size blocks called "pages."
- When a program accesses a piece of data, the OS checks if the page containing the data is in RAM. If not, it fetches the page from disk (in an area known as the swap space) and loads it into RAM.
- Page Table:
- The OS maintains a page table that maps virtual addresses to physical addresses. This allows the system to keep track of where each page is stored in RAM or on disk.
- Page Fault:
- When a program tries to access data on a page that is not currently in RAM, a page fault occurs. The OS then retrieves the required page from disk into RAM, which may involve swapping out another page to make room.
- Swapping:
- Swapping is the process of moving pages between RAM and disk. When RAM is full, the OS selects certain pages (usually the least recently used) to be swapped out to disk. This frees up space in RAM for other pages that are needed immediately.
- Advantages of Virtual Memory:
- Efficient Memory Use: It allows multiple programs to run simultaneously without running out of physical memory.
- Isolation: Each process gets its own virtual address space, providing protection and isolation from other processes.
- Flexibility: Programs can be larger than the physical memory available, as the OS can swap parts of the program in and out of RAM as needed.
- Disadvantages:
- Performance Overhead: The process of swapping pages in and out of RAM can cause delays, especially if the system is frequently accessing data not in RAM (a condition known as thrashing).
- Complexity: Implementing and managing virtual memory adds complexity to the OS.
How Virtual Memory Works:
- Address Translation:
- When a program uses a virtual address to access data, the OS translates this virtual address into a physical address using the page table.
- Memory Allocation:
- The OS allocates memory to processes using virtual memory. It ensures that processes do not interfere with each other's memory, providing a secure and stable environment.
- Demand Paging:
- The OS loads pages into memory only when they are needed, which is known as demand paging. This conserves RAM and improves efficiency.
Practical Example:
- Imagine you have 8 GB of RAM but are running applications that require 16 GB. Virtual memory allows the OS to use disk space to store parts of these applications, making it seem like you have more RAM than you actually do. When the OS needs to access data from the applications that are not currently in RAM, it will swap them from the disk into RAM, and vice versa.
Virtual memory is essential in modern computing, enabling systems to run large and complex applications efficiently, even with limited physical memory.
Dhanish Soni
53003230069