


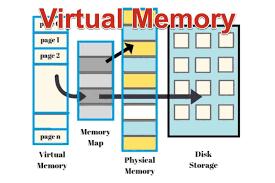
Virtual memory is a memory management technique used by operating systems to provide an application with the illusion of having a large, contiguous block of memory, even if the physical memory (RAM) is limited. It enables the system to use disk space (usually a portion of the hard drive or SSD) as an extension of RAM, allowing more processes to run concurrently than the available physical memory would otherwise permit.
Benefits of Virtual Memory:
Isolation and Protection: Virtual memory isolates each process’s address space, protecting them from each other and improving system security.
Efficiency: It allows the system to run larger applications and more processes than physical memory alone would support.
Flexibility: Programs can be written as if they have access to a large, contiguous block of memory, simplifying development and improving portability.
Challenges:
Overhead: Managing virtual memory introduces overhead, as the system must constantly translate virtual addresses to physical ones.
Performance: If the system relies heavily on swapping and paging (often called "thrashing"), it can lead to performance degradation since disk access is much slower than RAM access.
Virtual memory is a fundamental concept in modern operating systems, enabling more efficient use of hardware resources and providing a robust environment for multitasking and memory-intensive applications.