


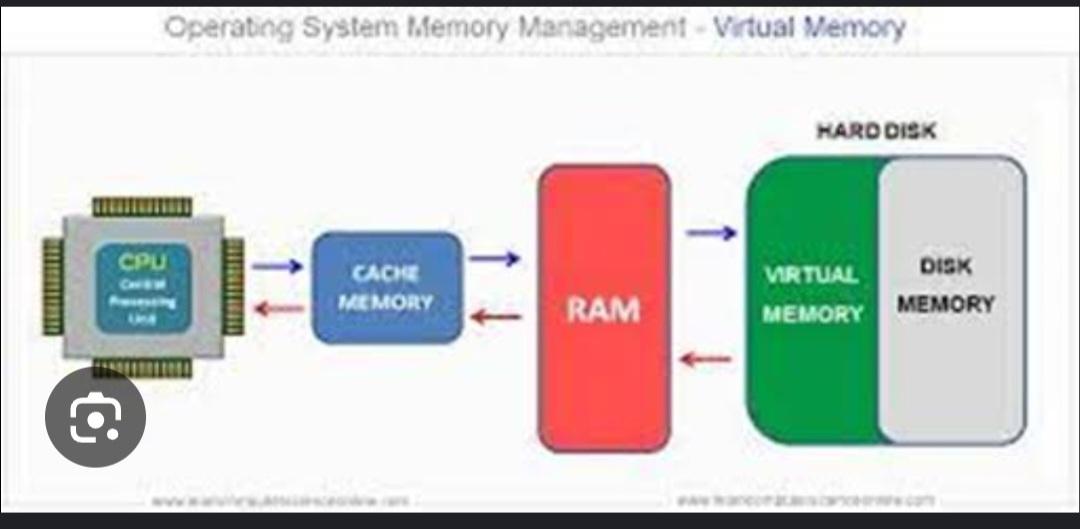
Virtual memory is a memory management technique used by operating systems to give the appearance of a large, continuous block of memory to applications, even if the physical memory (RAM) is limited. It allows the system to compensate for physical memory shortages, enabling larger applications to run on systems with less RAM.
It is a technique that is implemented using both hardware and software. It maps memory addresses used by a program, called virtual addresses, into physical addresses in computer memory.
There are two main types of virtual memory:
Paging divides memory into small fixed-size blocks called pages. When the computer runs out of RAM, pages that aren’t currently in use are moved to the hard drive, into an area called a swap file. The swap file acts as an extension of RAM. When a page is needed again, it is swapped back into RAM, a process known as page swapping. This ensures that the operating system (OS) and applications have enough memory to run
Segmentation divides virtual memory into segments of different sizes. Segments that aren’t currently needed can be moved to the hard drive. The system uses a segment table to keep track of each segment’s status, including whether it’s in memory, if it’s been modified, and its physical address. Segments are mapped into a process’s address space only when needed.