


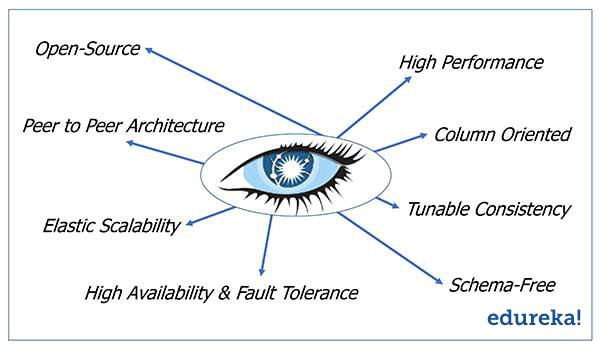
Data Model:
Scalability:
Performance:
Consistency vs. Availability vs. Partition Tolerance (CAP):
Data Volume:
Complexity of Queries:
Consistency Models:
Security and Compliance:
Cost and Licensing:
Backup and Disaster Recovery:
Future Growth and Flexibility:
Data Integrity and ACID Transactions:
Latency and Geographic Distribution:
Operational Complexity:
Development Ecosystem and Support: