As far as memory management is concerned, both unequal fixed-size partitions and variable-size partitions reflect inefficiencies. Unequal fixed-size partitions are the cause of internal fragmentation, which is when the memory space given to a process is not entirely used and as a result, there is some unused space within the partition. Variable-size partitions can, however, give rise to the problem of external fragmentation such that the free memory is distributed in small, non-contiguous blocks which makes it difficult to allocate the available spaces that are larger and contiguous.
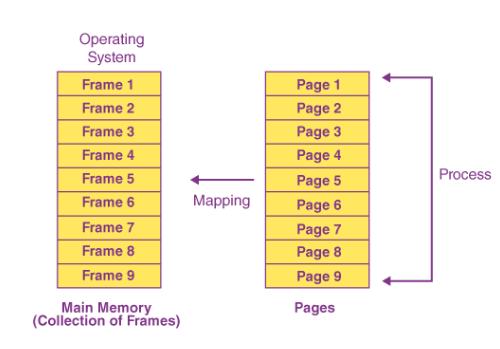
In order to come up with a solution to these problems, the “paging” notion is introduced. In paging, the main memory is split into equal fixed-size pieces that are called frames, and the processes are also split into the same size pages. This technique is a good way to fix the fragmentation problem. So, it is like this:
- Page and Frame Allocation: Each page of a process can be allocated to an arbitrary free frame in memory. For example, if the process has several pages and the memory space has free frames, the OS can place these pages into any free frames, irrespective of the physical location of the pages. Hence, the requirement of needing contiguous free memory blocks is avoided.
- Internal fragmentation: The main waste in paging is internal fragmentation, which is confined to the last page of a process if it is not completely full. Take for instance if’s last page consists of the allocated space only partially. In that case, the remainder is wasted). Within a page that is not being used, one might find a small area that is still closed and thus not being used. However, given that the pages are fixed in size, such a loss is restricted to the last page only and is usually very small in comparison with the losses resulting from variable-size partitions.
- Address Translation and Page Table: The operating system is in charge of the page table for each process, which translates logical addresses into physical addresses. The physical memory frame that contains each page of the process is explicitly stated in this table. The logical address is split up into a page number and an offset which tells the position of the traveled page. The page number is the one that is used to look up the corresponding frame through the page table, and then the offset is the one that is used to find the exact location within that frame.
- Handling Memory Allocation: Imagine a situation when a process is to be loaded, but the available contiguous memory is insufficient, paging is the solution. The OS can now place pages in all the frames that are available, and it is not necessary to have contiguous memory allocation. For instance, if a new process requires the production of more pages than there are contiguous free frames, the OS can load these pages into non-contiguous ones that are randomly distributed in memory. This flexibility is a significant advantage over partitioning schemes that require contiguous memory allocation.
In summary, paging solves the memory fragmentation problems by splitting the whole memory into fixed-size units and allowing free allocation of these units. The OS page tables, which map the logical addresses to physical addresses, are used to manage the memory efficiently and avoid the problems of internal and external fragmentation.