- Java Socket programming is used for communication between the applications running on different JRE.
- Java Socket programming can be connection-oriented or connection-less.
- Socket and ServerSocket classes are used for connection-oriented socket programming and DatagramSocket and DatagramPacket classes are used for connection-less socket programming.
- The client in socket programming must know two information:1) IP Address of Server, and 2)Port number.
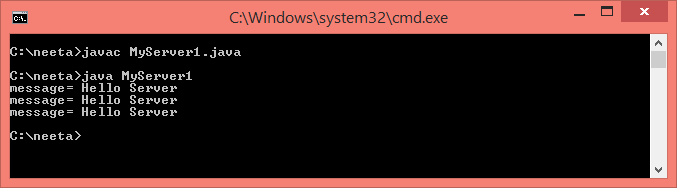
import java.io.*; import java.net.*; public class MyServer1 { public static void main(String[] args) { try { ServerSocket ss=new ServerSocket(6666); Socket s=ss.accept();//establishes connection DataInputStream dis=new DataInputStream(s.getInputStream()); String str=(String)dis.readUTF(); System.out.println("message= "+str); System.out.println("message= "+str); System.out.println("message= "+str); ss.close(); } catch(Exception e) { System.out.println(e); } } }
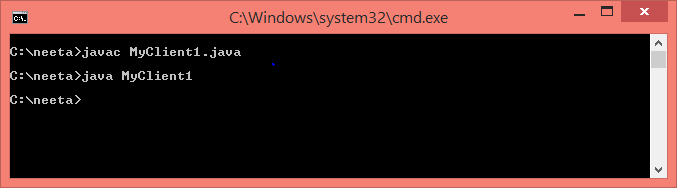
import java.io.*; import java.net.*; public class MyClient1 { public static void main(String[] args) { try { Socket s=new Socket("localhost",6666); DataOutputStream dout=new DataOutputStream(s.getOutputStream()); dout.writeUTF("Hello Server"); dout.flush(); dout.close(); s.close(); } catch(Exception e) { System.out.println(e); } } }