


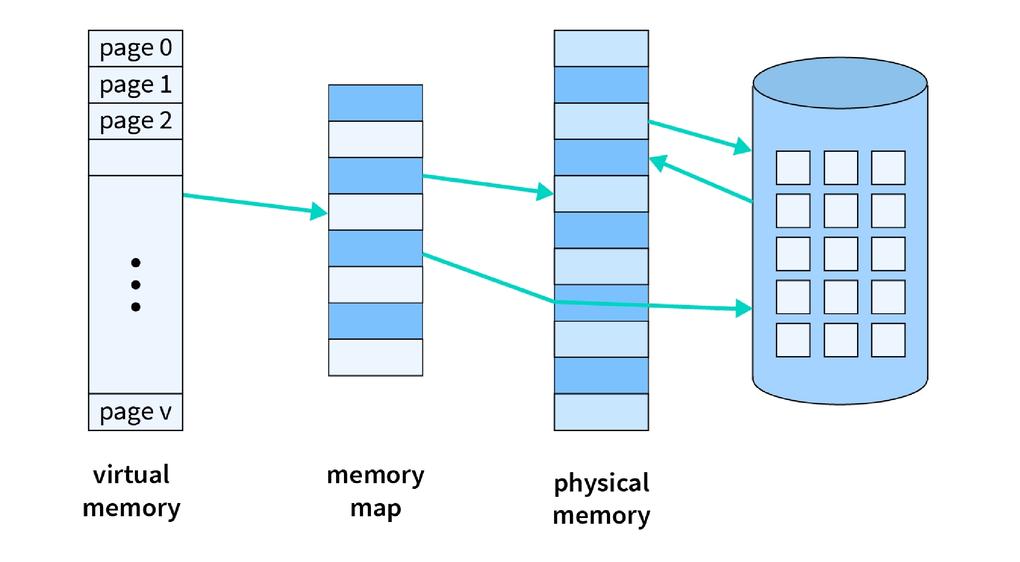
Types of Virtual Memory
Paging separates memory into little fixed-size squares called pages. When the computer runs out of Smash, pages that aren't right now in utilize are moved to the difficult drive, into an region called a swap record. The swap record acts as an expansion of Smash. When a page is required once more, it is swapped back into Slam, a prepare known as page swapping. This guarantees that the working framework (OS) and applications have sufficient memory to run.
Segmentation partitions virtual memory into portions of diverse sizes. Portions that aren't as of now required can be moved to the difficult drive. The framework employments a portion table to keep track of each segment's status, counting whether it's in memory, if it's been adjusted, and its physical address. Sections are mapped into a process's address space as it were when needed.