


Have you ever been out and about and needed to connect to Wi-Fi? You have a limited time, so it's important that you find the closest network with the strongest connection. Once you do, you'll see a little exclamation point next to the password field - which is presumably there so that no one can hack into your personal information. But, what if that exclamation point was actually put there to deceive you? What if it was there because the Wi-Fi network you were connecting to was set up by an attacker?
What is an Evil Twin Attack?
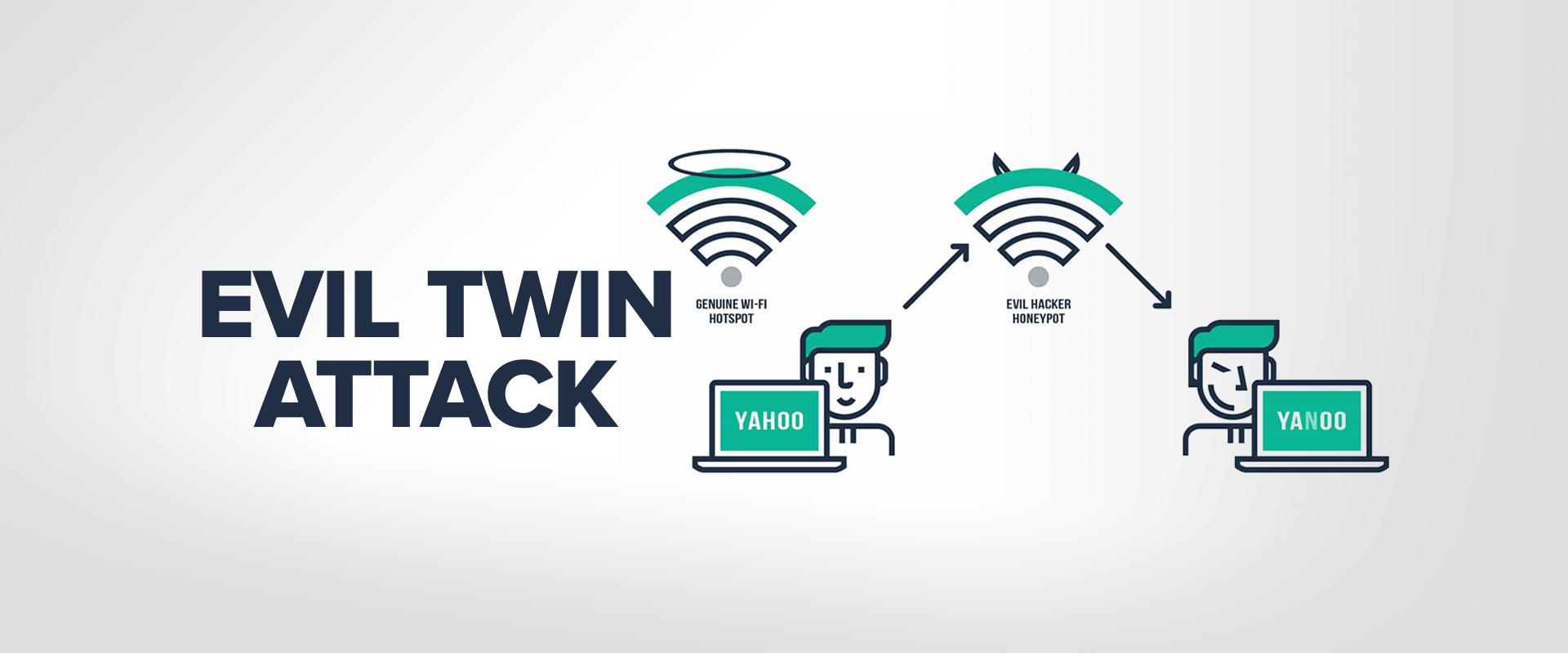
An evil twin attack is a type of cyberattack where an attacker creates a duplicate of a legitimate wireless access point (AP) and uses it to lure victims into connecting to it. The attacker can then intercept and monitor their traffic or even inject malicious content into it.
Evil twin attacks are a serious threat because they are relatively easy to carry out and can be very difficult for victims to detect. In most cases, the only way to tell the difference between a legitimate AP and an evil twin is by looking at the MAC address (a unique identifier assigned to every wireless device).
Fortunately, there are some steps you can take to protect yourself from evil twin attacks. For example, you can use a VPN or other encryption methods to encrypt your traffic. You should also be cautious about connecting to public Wi-Fi networks, especially if you are not familiar with them.
How Do They Work?
Most people have heard of the term “hacking”, but not everyone is familiar with the term “evil twin attack”. So, what exactly is an evil twin attack? Evil twin attacks are a type of spoofing attack that occurs when an attacker creates a duplicate of a legitimate wireless access point (AP) and uses it to trick users into connecting to it.
These types of attacks have become increasingly popular in recent years as they are relatively easy to carry out and can be very difficult for users to detect. Once a user connects to the evil twin AP, the attacker can then intercept and/or modify any data that is being sent or received.
There are a few different ways that evil twin attacks can be carried out. One common method is for attackers to use easily available software to create a fake AP that mimics the SSID (name) of a legitimate AP. Another method is to physically set up a rogue AP near the targeted area. This can be done by using a device that broadcasts a strong signal or by placing the AP near enough to the legitimate AP that it will have a stronger signal than the legitimate AP.
One way to protect yourself from evil twin
Why Are they Dangerous?
When it comes to cyberattacks, there is always something new and dangerous around the corner. The latest trend in attacks is known as "evil twin" or "spoofing" attacks. Here's what you need to know about these dangerous attacks and why they are on the rise.
Evil twin attacks get their name from the fact that they seek to imitate a legitimate website or service in order to trick users into entering their login credentials or other sensitive information. These attacks are particularly dangerous because they can be very difficult to spot. The best way to protect yourself from an evil twin attack is to be aware of the signs and to know how to spot them.
One of the most common signs of an evil twin attack is a sudden change in the URL of a website that you frequently visit. If you notice that the URL has been changed, especially if it includes a new domain name, be wary. Another sign to look for is unusual activity on your account after visiting a website or entering your login information. If you see anything out of the ordinary, report it to the website or service immediately and change your password.
Evil twin attacks are on the rise because they are an easy way for attackers to gain access to sensitive
How to Reduce the Risk of Falling Victim to an Evil Twin Attack:
As we become increasingly reliant on technology in our everyday lives, so too do cybercriminals find new and innovative ways to exploit vulnerabilities. One of the latest techniques to emerge is the evil twin attack, which can be used to gain access to sensitive information or carry out other malicious activities.
So, what is an evil twin attack? Put simply, it is a type of spoofing attack whereby the attacker creates a fake wireless access point (WAP) that masquerades as a legitimate one. When users connect to the WAP, they are unknowingly giving the attacker access to their data.
There are a number of ways you can reduce the risk of falling victim to an evil twin attack. Firstly, be aware of your surroundings when using public Wi-Fi and avoid connecting to any networks that you don’t recognize. Secondly, make sure your anti-virus and anti-malware software is up-to-date as this will help to protect you against any malicious software that may be used in an attack. Finally, always use a VPN when connecting to public Wi-Fi as this will encrypt your data and make it much more difficult for an attacker to intercept it.