SIEM Empowering Security with deeper detection and faster response
Security today is a perfect blend of people process and technology. People have to follow process and use technology to secure our critical IT infrastructure and respond to threats in well-organized fast we can detect and remediate the hack.
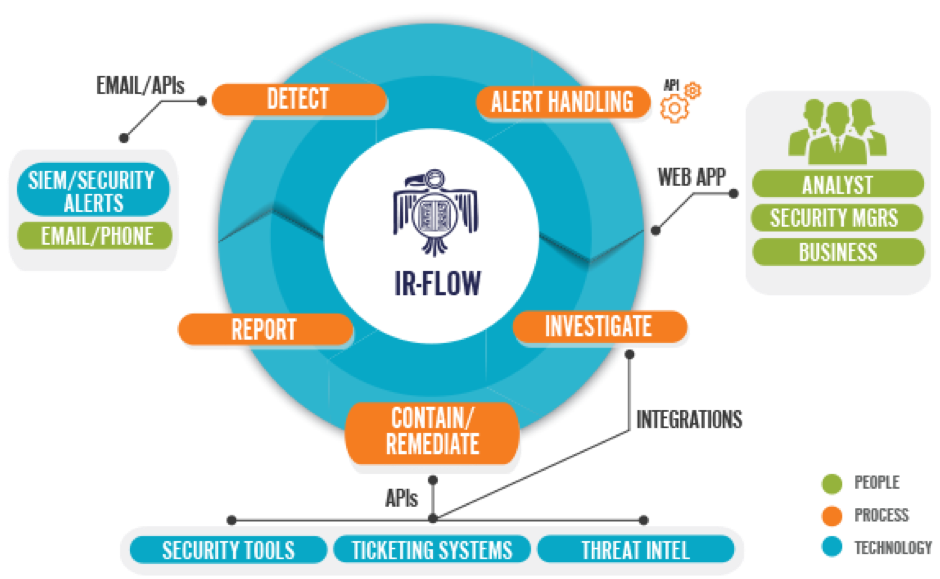
As we know IT infrastructure can grow in size and complexity which makes it difficult to implement and manage security. The basic actionable intelligence we have in our system is the logs of the system.
These logs record everything .with a right practise of logging storing and analysing these logs we can detect prevent and remediate threats. To manage the it security needs of organisation we need to implement SIEM solutions
SIEM stands for
"Security Incident and Event Management"
Few examples of these solutions are :
HP Arcsight, RSA SA(dell), IBM Qradar, Splunk
SIEM objective:
SIEM solutions have been around for many years and they were designed primarily for two objectives:
- Collect, analyze, report and store log data from hosts, applications and security devices to support security policy compliance management and regulatory compliance initiatives
- Process and correlate in real time event data from security devices, network devices and systems to identify security issues that pose the biggest risk to an organization .
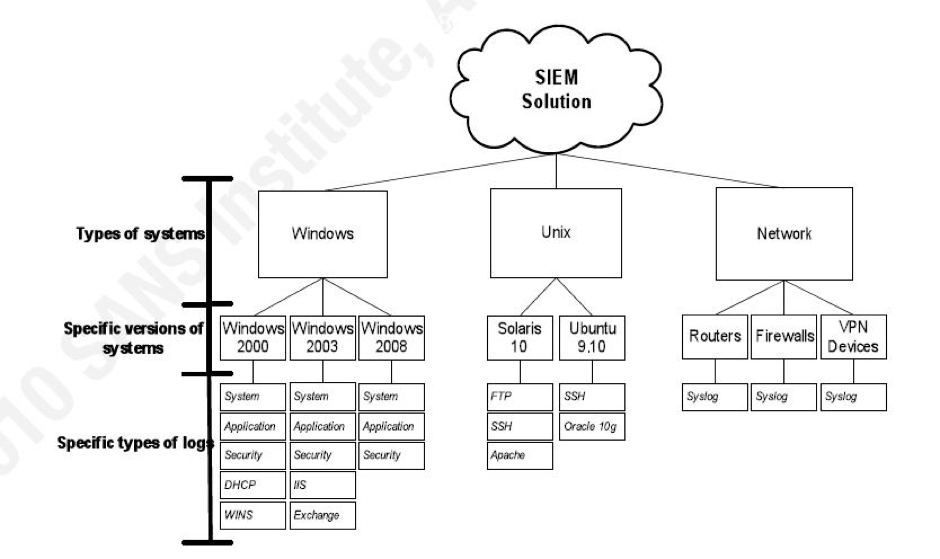
To fulfil the above objective we need data from the following data sources
Data Sources –
Full Packet Capture, NetFlowand Logs
We also need visibility of our environment having Threat Vectors – Endpoint, Network and Cloud.
SIEM Architecture & terms
Collection, Aggregation, Normatisation, Correlation, EPS
Collection layer is where all logs are feed into the siem solution it uses two technologies PUSH , PULL Push when a device is able to send its logs to the SIEM eg SPAN Checkpoint OLE etc. Pull is when the collector has to register and get logs to siem solution e.g. windows snare etc.
Since the number of logs created by our IT devices is huge in number we need optimize way to store and retrieve our security related logs. We make use of process of aggregation. Similar logs are stored with a number describing the number of events .we can set thresholds to be alerted after aggregation . The logs created by different machines have different format which makes it difficult to manage and detect alerts syslog of cisco is different from that of checkpoint .Normalisation maps these logs to a common event format on which co relation can be applied .
Correlation is a process which helps use to distinguish between a false positive and a true incident False positive can be termed as a false detection of a possible threat. Incident is termed as an event that cause disruption to our Infrastructure. Using correlation alerts are created in siem solutions
E.g. of alerts:
Windows machine created /deleted
Virus detected
Web attack detected
EPS events per second is a parameter which is used to know in a second how many events does a data source create. This information is also used to decide on how much storage would our SIEM consume
 Conclusion
Conclusion
In many instances, organizations go through multiple SIEM deployments to arrive at the Same level of understanding as the TDBUMO process provides but with Significantly more effort, more financial investment,
And more Resource utilization. As mentioned previously, “garbage in, garbage out” is often Used to
Describe SIEM correlation. As it is with correlation, poor analysis andPoorplanning Will only result in poor SIEM Coverage and performance, i.e., “garbage in, garbage out”.




 As we know IT infrastructure can grow in size and complexity which makes it difficult to implement and manage security. The basic actionable intelligence we have in our system is the logs of the system.
These logs record everything .with a right practise of logging storing and analysing these logs we can detect prevent and remediate threats. To manage the it security needs of organisation we need to implement SIEM solutions
SIEM stands for "Security Incident and Event Management"
Few examples of these solutions are :
HP Arcsight, RSA SA(dell), IBM Qradar, Splunk
As we know IT infrastructure can grow in size and complexity which makes it difficult to implement and manage security. The basic actionable intelligence we have in our system is the logs of the system.
These logs record everything .with a right practise of logging storing and analysing these logs we can detect prevent and remediate threats. To manage the it security needs of organisation we need to implement SIEM solutions
SIEM stands for "Security Incident and Event Management"
Few examples of these solutions are :
HP Arcsight, RSA SA(dell), IBM Qradar, Splunk
 Conclusion
In many instances, organizations go through multiple SIEM deployments to arrive at the Same level of understanding as the TDBUMO process provides but with Significantly more effort, more financial investment,
And more Resource utilization. As mentioned previously, “garbage in, garbage out” is often Used to
Describe SIEM correlation. As it is with correlation, poor analysis andPoorplanning Will only result in poor SIEM Coverage and performance, i.e., “garbage in, garbage out”.
Conclusion
In many instances, organizations go through multiple SIEM deployments to arrive at the Same level of understanding as the TDBUMO process provides but with Significantly more effort, more financial investment,
And more Resource utilization. As mentioned previously, “garbage in, garbage out” is often Used to
Describe SIEM correlation. As it is with correlation, poor analysis andPoorplanning Will only result in poor SIEM Coverage and performance, i.e., “garbage in, garbage out”.