Defination:
Ethical hacking is an authorized attempt to gain unauthorized access to computer system, appliction or data. When we talk about Ethical Hacking, It is explicitly implied that we are talking about hacking that is based on ethical or moral values, without any ill intent or purpose. Ethical hacking is a process of taking active security measures to defend or protect systems from hackers with malicious intensions on data privacy. This process will helps to identify security vulnerabilities which can then be resolved before a malicious attackers has the opportunity to exploit them.
Fundamental challanges to these security experts are finding weknesses and deficiencies in running and upcoming systems, applications, software and addressing them pro-actively. Ethical hacking is widely used as penetration testing to identify the vulnerabilities, risk and highlight the holes to take remedial actions against attacks.
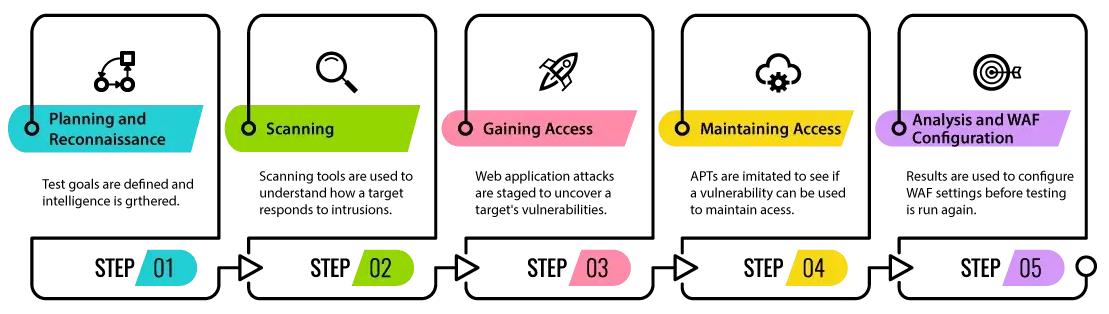
Phases of Ethical Hacking: