


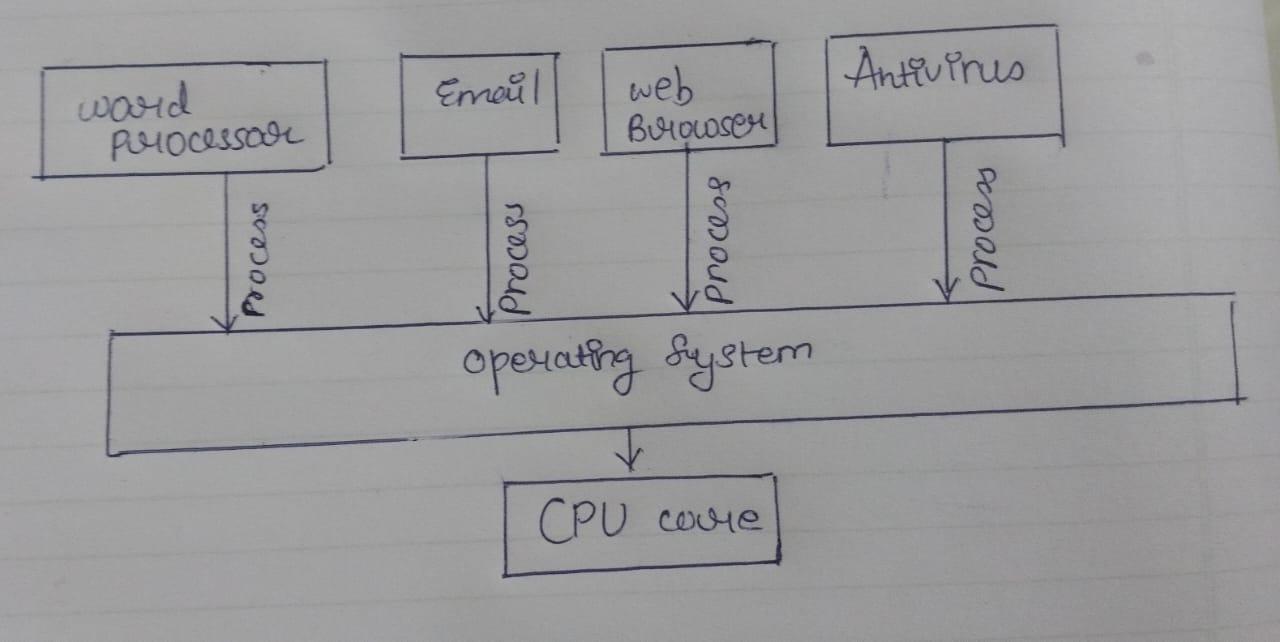
Opertaing Systems are the backbone of the IT technology. Without the Operating System we cannot perform any tasks. It helps us to manage both hardware and software by providing us the essential services for computer programs.Just like how human body cannot perform any task without backbone(spinal cord), similarly It technology is nothing without the Operating system
History of Operating Systems:
The concept of Operating systems can into the picture in the early days of computer in the year 1950s and 1960s. The first operating system was GM-NAA I/O, which was basically developed to perfoem input output operations. Later than that it paved its way for the development and a result of that we are blessed with operating system that we use now.
Functions of an Operating System:
Types of Modern Operating Systems:
Trends in Modern operating systems:
1. cloud integration:
Modern Operating system are increasingly including the cloud services. It allows for seamless data synchronization, backup and one can accesss ths data anywhere and at anyime. some of the examples are like Windos has OneDrive, macOS has icloud etc. iIt make easy for the user to store and access the data as per their convenience.
2. Security Enhancements:
With increase in the cyber threats it becomes important to protect the data . The Modern Operating system are focusing heavily on security. This includes various features like Enhanced encryptions, frequent security updates etc.
3. Artificial Intelligence and machine Learning:
Os have also started to incorporate the AI nd Ml to improve the users experience. This includes the personalized content delivery, intelligent system management, etc. few examples of the same are Microsoft's Cortana and Apple's Siri. this provides us with various functions are Siri automatically dials the phone call on giveen order, plays the music you ask. These things just enhance the user's experience.
4. Containerization:
Containerization is changing the way of deploying and managing the applications. Containers package applications along with everything they need to run and also make sure that they work the same way everywhere. Linux system are leading this trend.
Conclusion:
Modern Operating System are backbone of IT technology allowing the complex interaction between the hardware and the software . From the destop environment to mobile platforms they continue tu evolve for enhancing the user experience.