


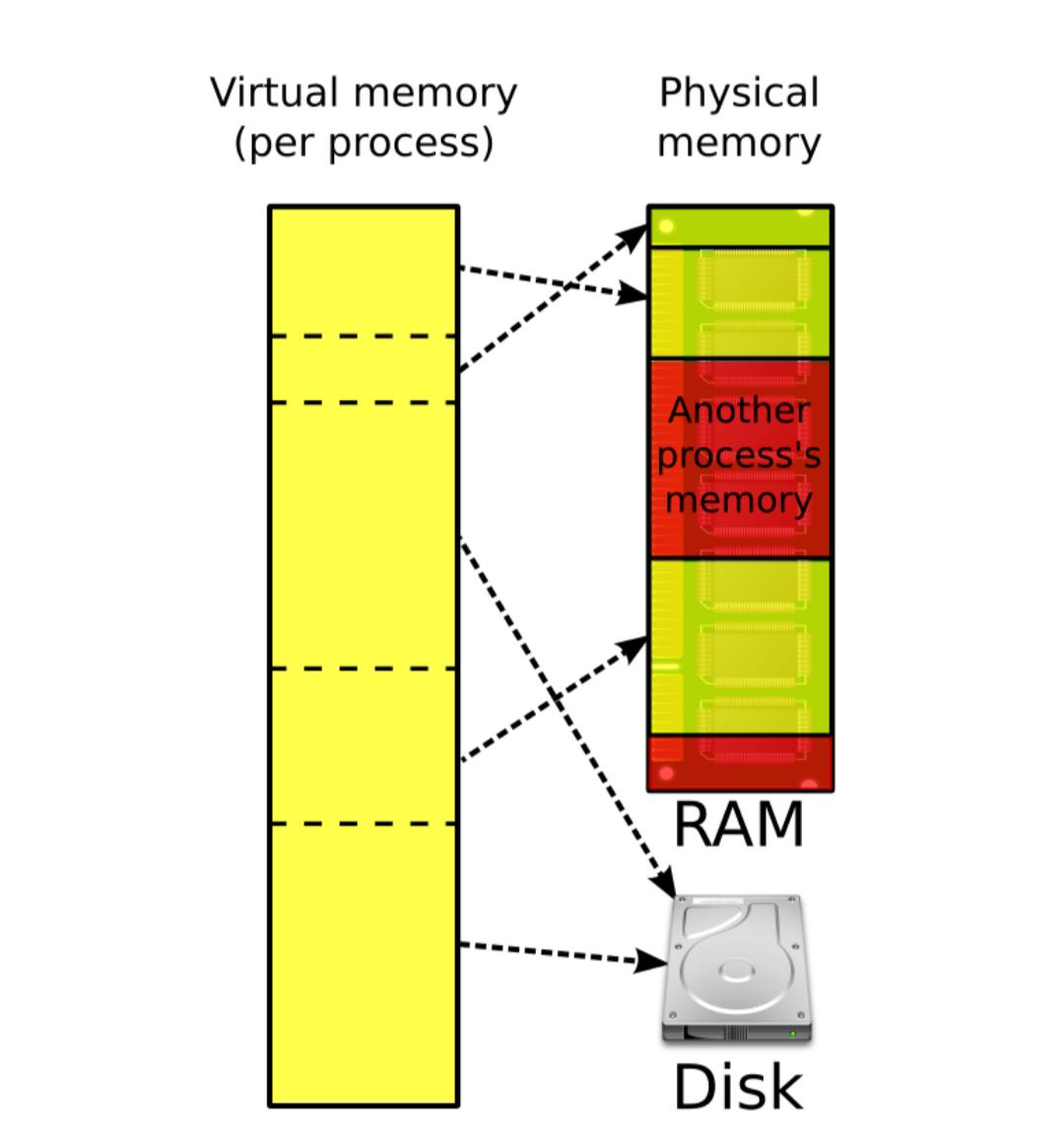
Virtual memory is a crucial concept in operating systems that allows for the efficient management of a computer's memory resources. It enables systems to execute larger applications or multiple applications simultaneously, even when the physical memory is limited.
Virtual memory operates primarily through two techniques: paging and segmentation.
- Paging divides the virtual memory into fixed-size pages and maps them onto physical frames in RAM. When a program needs data that isn’t currently in RAM, the OS retrieves it from disk storage (swap space) and loads it into RAM.
- Segmentation involves dividing the virtual address space into segments based on logical divisions, such as functions or objects, which can vary in size
-Benefits:
- Increased Effective Memory Size: Virtual memory allows systems to run larger applications than could fit into RAM.
- Isolation and Protection: Each process operates in its own virtual address space, preventing them from interfering with each other’s memory.
- Efficient Use of RAM: By keeping only active pages in physical memory and swapping inactive ones out, the system can maintain responsiveness even under heavy load.
-While virtual memory offers significant advantages, it can also introduce performance overhead:
- Page Faults: When a program accesses a page not currently in RAM, a page fault occurs, leading to delays as the system retrieves data from disk.
- Thrashing: If the system spends more time swapping pages in and out than executing processes, performance degrades significantly.
systems running database management systems (DBMS) benefit from virtual memory when handling large datasets that exceed physical memory limits.
Additionally, operating systems like Windows, Linux, and macOS implement sophisticated algorithms for page replacement (e.g., Least Recently Used - LRU), which significantly impact how well these systems perform under various conditions
53003230100
Disha parekh