


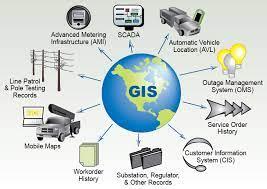
A geographic information system (GIS) consists of integrated computer hardware and software that store, manage, analyze , edit, output, and visualize geographic data. Much of this often happens within a spatial database, however, this is not essential to meet the definition of a GIS. In a broader sense, one may consider such a system also to include human users and support staff, procedures and workflows, the body of knowledge of relevant concepts and methods, and institutional organizations.
A Geographic Information System (GIS) is a computer system that analyzes and displays geographically referenced information. It uses data that is attached to a unique location.
GIS technology applies geographic science with tools for understanding and collaboration. It helps people reach a common goal: to gain actionable intelligence from all types of data.
Maps are the geographic container for the data layers and analytics you want to work with. GIS maps are easily shared and embedded in apps, and accessible by virtually everyone, everywhere.
GIS integrates many different kinds of data layers using spatial location. Most data has a geographic component. GIS data includes imagery, features, and basemaps linked to spreadsheets and tables.
Spatial analysis lets you evaluate suitability and capability, estimate and predict, interpret and understand, and much more, lending new perspectives to your insight and decision-making.
Apps provide focused user experiences for getting work done and bringing GIS to life for everyone. GIS apps work virtually everywhere: on your mobile phones, tablets, in web browsers, and on desktops.