


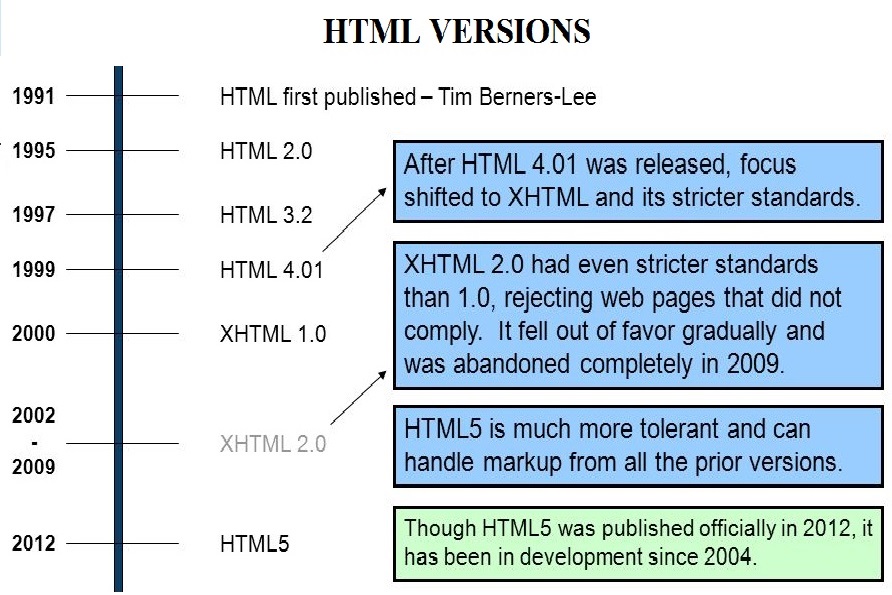
STRUCTURE COMPARISON
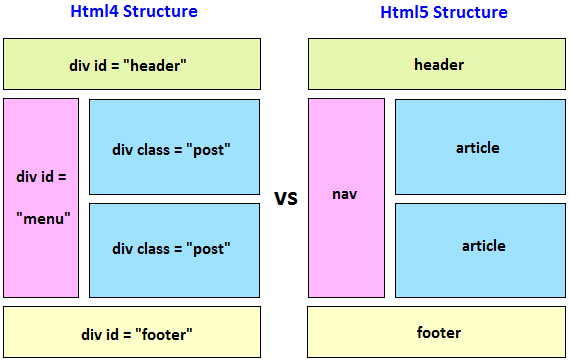
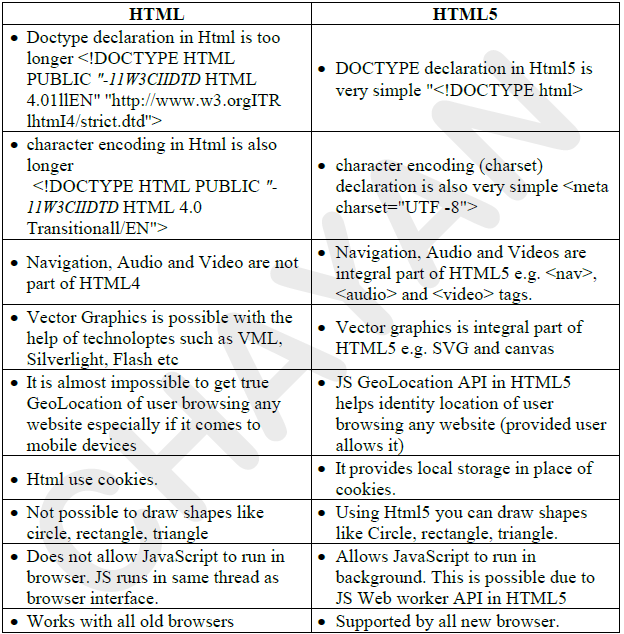
FEATURE COMPARISON
Review on Cyber Forensics and its Analysis Tools

Starvation

Life

Digital black market or dark net poses a national security threat?

TEAMWORK

Unlocking the Secrets: Basic Operations of Computer Forensic Laboratories
Why Soft Skills Matter as Much as Grades?

Constrains in service design

FRIENDSHIP
Direct Memory Access

Memory Hierarchy
SEIZING DIGITL EVIDENCE AT THE SCENE
Memory Management Techniques
What is Password Cracking ? and it's Techniques.

EVOLUTION OF THE MIRCOPROCESSOR
Data Structures
15 Interesting Facts about India

5 Stages of Digital Marketing
5 Things I As A Dentist Would Never Do (And What You Can Learn From It)

Deadlock in Operating systems
MQTT (MQ Telemetry Transport) in Data Science
Social engineering in cyber security
indian premier league

Blog on health and fitness

Video games
Facebook Shut Down an AI Program!!! Facebook AI bots became Terminators???

Key to success in Sports

Security issues in Sensor Networks and gathering admissible evidence in Network Forensics
VIRTUAL MACHINE
Why Consistency in Eating Habits Matters and How Meal Maharaj Makes It Easy

Beauty of indian railway

Khau Galli – Vile Parle

Brilliant WhatsApp Features Upcoming in 2023
CRISP-DM Methodology

Review on Recovering Deleted Files

Evolution of Operating System
Threads
Functions Of Operating Systems
What Your Music Taste Reveals About Your Personality

De-Coding Love

Elements and Principles of Photography

Memory input output management
