


Memory management in computing refers to the process of controlling and coordinating computer memory, assigning blocks of memory to various running programs to optimize overall system performance. It involves several key activities:
1. Allocation: Assigning memory to programs when they request it. This can be done statically (before runtime) or dynamically (during runtime).
2. Deallocation: Releasing memory back to the system when a program no longer needs it, so that it can be reused by other programs.
3. Garbage Collection: Automatically identifying and freeing memory that is no longer in use by the program, often handled by a garbage collector in languages like Java or Python.
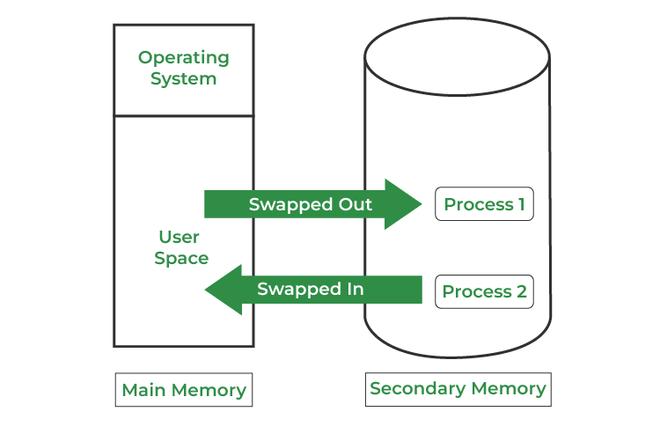
4. Paging and Segmentation: Techniques used by the operating system to manage memory efficiently, ensuring that programs can run even when they require more memory than is physically available by using disk space as a temporary extension of RAM.
5. Virtual Memory: A memory management technique that gives an application the impression it has contiguous working memory while actually using physical memory fragments and disk space.
6. Memory Leaks: A situation where memory is not properly deallocated, leading to a gradual reduction in available memory, which can slow down or crash a system.
Effective memory management is crucial for system stability, performance, and the ability to run multiple applications simultaneously.