


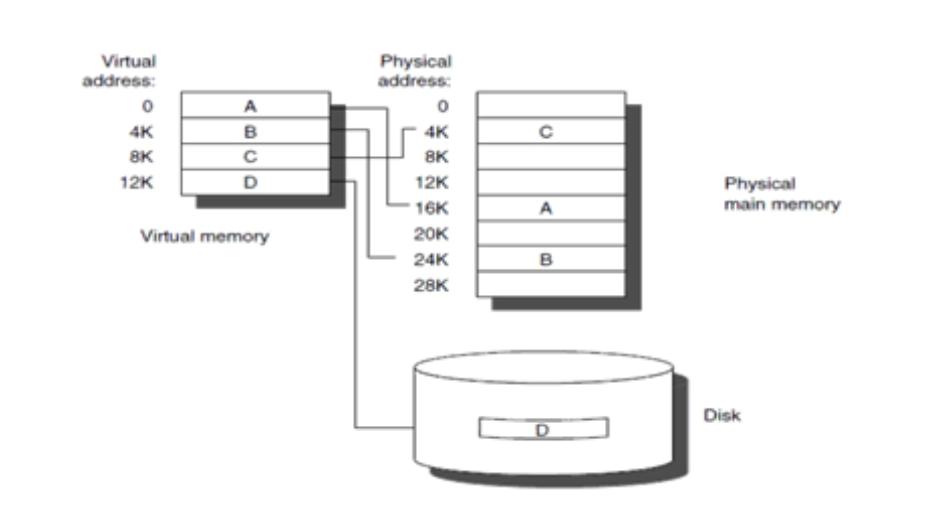
In computing, virtual memory, or virtual storage, is a memory managament technique that provides an idealized abstraction of the storage resources that are actually available on a given machin which, creates the illusion to users of a very large (main) memory.
The computer's oprating system, using a combination of hardware and software, maps momery addresses used by a program, called virtual addresses, into physical addresses in computer memory. main storage, as seen by a process or task, appears as a contiguous address space or collection of contiguous segments. The operating system manages virtual address spaces and the assignment of real memory to virtual memory.
The primary benefits of virtual memory include freeing applications from having to manage a shared memory space, ability to share memory used by libraries between processes, increased security due to memory isolation, and being able to conceptually use more memory than might be physically available, using the technique of paging or segmentation.
Virtual memory makes application programming easier by hiding fragmentation of physical memory, by delegating to the kernel the burden of managing the memory hierarchy. (eliminating the need for the program to handle overlays explicitly); and, when each process is run in its own dedicated address space, by obviating the need to relocate program code or to access memory with relative addressing.
memory virtualization can be considered a generalization of the concept of virtual memory.
1.The degree of Multiprogramming will be increased.
2. User can run large application with less real RAM.
3. There is no need to buy more memory RAMs.