


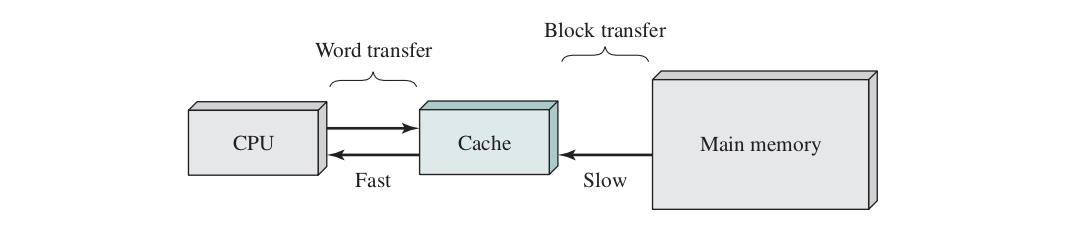
Cache memory is a small, high-speed storage location that stores frequently accessed data and instructions, improving overall processing speed by reducing the time it takes for the CPU to retrieve this information from the main memory.
It is a faster and smaller segment of memory whose access time is as close as registers. In a hierarchy of memory, cache memory has access time lesser than primary memory. Generally, cache memory is used as a buffer.Cache memory is a small, high-speed storage layer situated between the CPU and the main memory (RAM). It is designed to temporarily hold frequently accessed data and instructions, allowing for faster data retrieval and improved overall system performance.
Key Features of Cache Memory
1.Speed: Faster than the main memory (RAM), which helps the CPU retrieve data more quickly.
2.Proximity: Located very close to the CPU, often on the CPU chip itself, reducing data access time.
3.Function: Temporarily holds data and instructions that the CPU is likely to use again soon, minimizing the need to access the slower main memory.
Benefits of cache memory
1. Increased Speed: By storing frequently accessed data and instructions closer to the CPU, cache memory significantly reduces the time needed for data retrieval, speeding up overall system performance.
2. Efficiency: It helps in reducing the load on the main memory, allowing the system to handle multiple tasks more efficiently.
3. Reduced Latency:Cache memory minimizes the delay in data access, which is crucial for time-sensitive applications and real-time processing.
4. Enhanced Multitasking: By speeding up data access, cache memory improves the system's ability to manage and execute multiple processes simultaneously.
5. Energy Savings:Faster data access can lead to reduced power consumption since the CPU spends less time in high-power states waiting for data.
6. Improved User Experience:Overall system responsiveness and application performance are enhanced, leading to a smoother and more efficient user experience.