


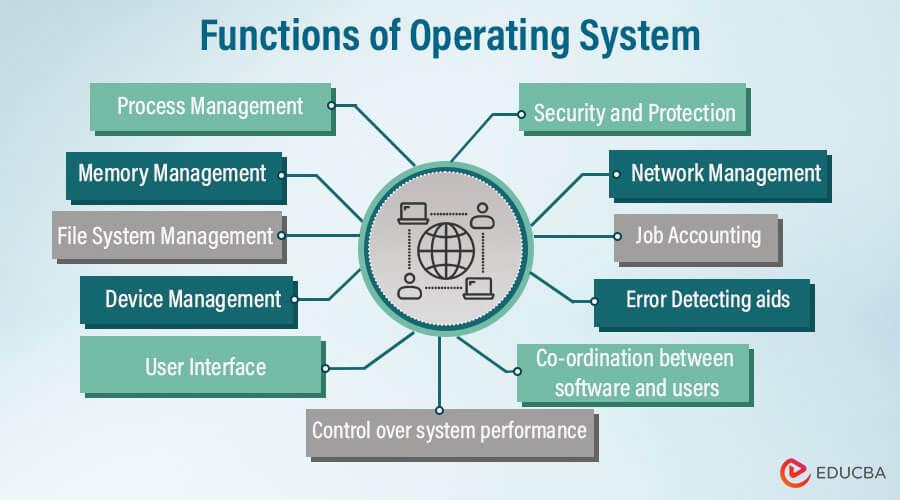
The operating system is a connecting medium between the user and the hardware. It helps the users to access the hardware in an efficient manner. It also makes sure that all the computer resources will be used in an efficient and smooth way without any problems
******The operating system provides various functionalities, which are discussed below:****
Controlling System Performance One of the most important functions of the operating system is controlling the system's health. For this purpose, it monitors and observes the delay time between a service being requested and the requested service being served. This delay time is reduced as much as possible to improve the overall performance of the system.
***Memory Management****
In a computer system, we have primary memory, which is also called main memory, and it is made by the sequence of bytes. Each byte in the main memory has a unique address which helps it to check if it is occupied or not. For executing each program in its computer system, it should be in the main memory. Operating systems can easily check which bytes of main memory are empty and which are not. So it allocates the main memory for the program execution, and when the program is completed or terminated, then it deallocates the memory. Operating systems also keep a record that which byte of memory is assigned to which program
****Device Management*****
The operating system manages the communication between the computer system and the peripheral devices connected to the I/O port of the system. Peripheral devices use their respective drivers to communicate with the system. The operating system determines which program or process is accessed by which connection and device. It also makes sure when a program is executed or terminated, it will stop the communication between the device and the computer system.
*****Coordination between other software and the user******
There is other software in the system which is coordinated by the operating system so that users can access them efficiently, like assemblers, compilers, etc.
******Process Management******
The process is a program under the execution. The operating system manages all the processes so that each process gets the CPU for a specific time to execute itself, and there will be less waiting time for each process. This management is also called process scheduling.