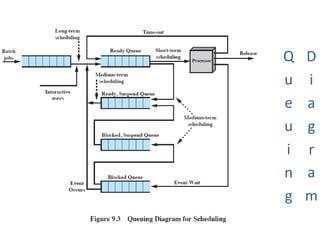
Uniprocessor scheduling is a key concept in operating systems where a single processor (CPU) handles multiple tasks by deciding the order in which they are executed. Since the CPU can only perform one task at a time, it needs an organized way to switch between different tasks to make sure all of them are completed efficiently and fairly.
Here are some important details about the scheduling methods:
1. First-Come, First-Served (FCFS): This is the simplest method, where tasks are handled in the order they arrive. However, if a long task comes first, it might delay others, which is called the "convoy effect."
2. Shortest Job Next (SJN): The CPU picks the task with the shortest processing time. This method reduces waiting time for shorter tasks, but it might cause longer tasks to be delayed indefinitely, a problem called "starvation."
3. Round Robin (RR): In this method, each task gets a fixed amount of time to run (called a time quantum). If the task isn’t finished in that time, it goes to the back of the line, and the CPU moves to the next task. This makes sure no task is ignored for too long.
4. Priority Scheduling: Tasks are assigned a priority level, and the CPU handles higher-priority tasks first. Lower-priority tasks might have to wait longer if high-priority ones keep coming, but it's useful for systems where certain tasks need immediate attention.
Some other key terms:
- **Preemptive Scheduling**: The CPU can pause a task mid-way and switch to a higher-priority task.
- Non-preemptive Scheduling: Once a task starts, it runs to completion before the next one can start.
The goal of uniprocessor scheduling is to maximize CPU utilization, minimize waiting time, and provide a good user experience by making sure tasks are completed in a timely manner.