


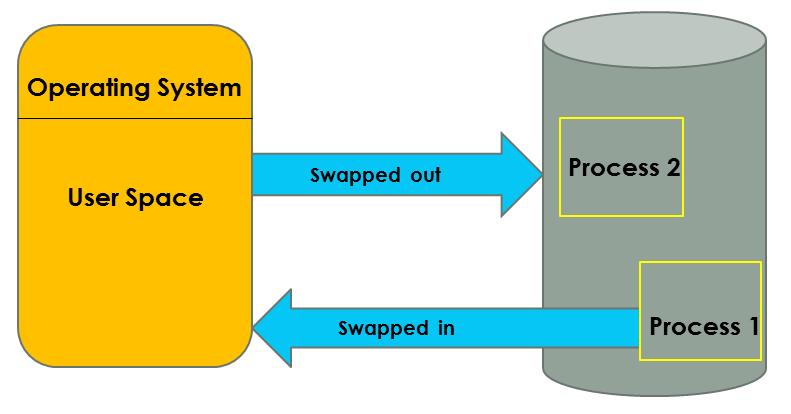
Memory management in an operating system is a crucial function that involves handling and coordinating computer memory. Here are some key points about it:
Memory management ensures that the system runs efficiently and that processes have the necessary memory to execute without interfering with each other2