



In our daily lives we tend to enter passwords over multiple places including our bank accounts, mobile Lock Screen, website or application login and many more places.
Have you ever wondered, how the passwords are stored or how they travel through the network?
If all information were plaintext and had no encryption or cryptography surrounding it, sensitive materials like password information, health records, and even bank account information could be stolen and sold to the highest bidder. One of the first steps of basic security hygiene is to not store sensitive data in plaintext—especially passwords. This is where password hashing comes in.
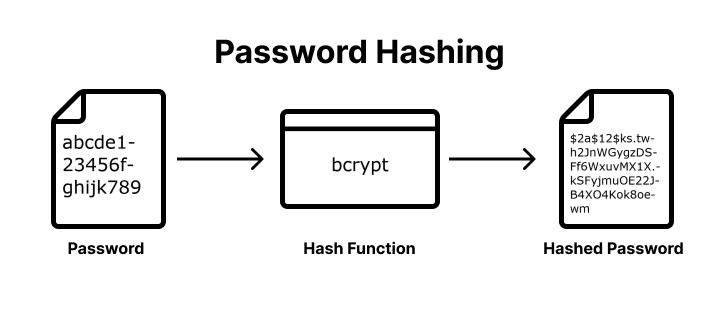
Password hashing is used to verify the integrity of your password, sent during login, against the stored hash so that your actual password never has to be stored. Not all cryptographic algorithms are suitable for the modern industry.
If the passwords are hashed then how are accounts compromised?
There are many ways to hack into an account. Password cracking is one of them – involves using various computational and other methods to break through the password authentication step.
Even the passwords can be cracked by using different methods. Password cracking means recovering passwords from a computer or from data that a computer transmits. This doesn’t have to be a sophisticated method. A brute-force attack where all possible combinations are checked is also password cracking.
Rainbow Tables
Rainbow tables are tables of reversed hashes used to crack password hashes. Computer systems requiring passwords typically store the passwords as a hash value of the user's password. When a computer user enters a password, the system hashes the password and compares it to the stored hash.
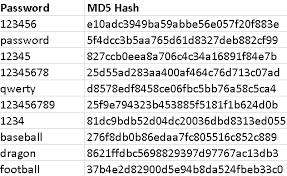
It is a table of commonly used password and their hash combinations to match with the plain text and guess the password. These are easily available on google and are downloadable in csv form
Now, here, there is something to be noted! The passwords cracked using the methods given above are for unsalted hashed password.
Yeah! There exists a concept called salting, which makes it impossible to use lookup tables and rainbow tables to crack a hash.
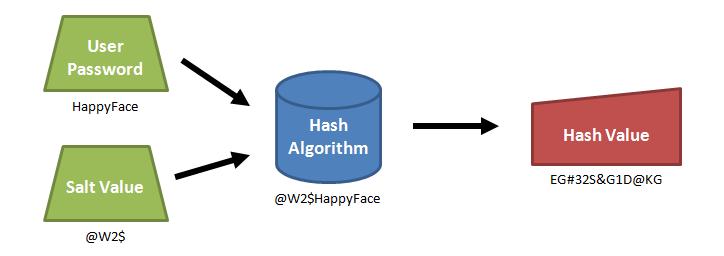
Lookup tables and rainbow tables only work because each password is hashed the exact same way. If two users have the same password, they'll have the same password hashes. We can prevent these attacks by randomizing each hash, so that when the same password is hashed twice, the hashes are not the same.
We can randomize the hashes by appending or prepending a random string, called a salt, to the password before hashing. As shown in the example above, this makes the same password hash into a completely different string every time. To check if a password is correct, we need the salt, so it is usually stored in the user account database along with the hash, or as part of the hash string itself.
The salt does not need to be secret. Just by randomizing the hashes, lookup tables, reverse lookup tables, and rainbow tables become ineffective. An attacker won't know in advance what the salt will be, so they can't pre-compute a lookup table or rainbow table. If each user's password is hashed with a different salt, the reverse lookup table attack won't work either.