MEMORY MANAGEMENT REQUIREMENT
(I) Memory management is a critical function of an operating system (OS) that handles the allocation and deallocation of memory resources to various processes and ensures optimal use of the computer's memory.
(II) Memory management keeps track of the status of each memory location, whether it is allocated or free.
(III) It allocates the memory dynamically to the programs at their request and frees it for reuse when it is no longer needed.
(IV) Memory management is meant to satisfy some requirements that we should keep in mind.
(V) Here are the key requirements for memory management in an operating system:
Relocation:
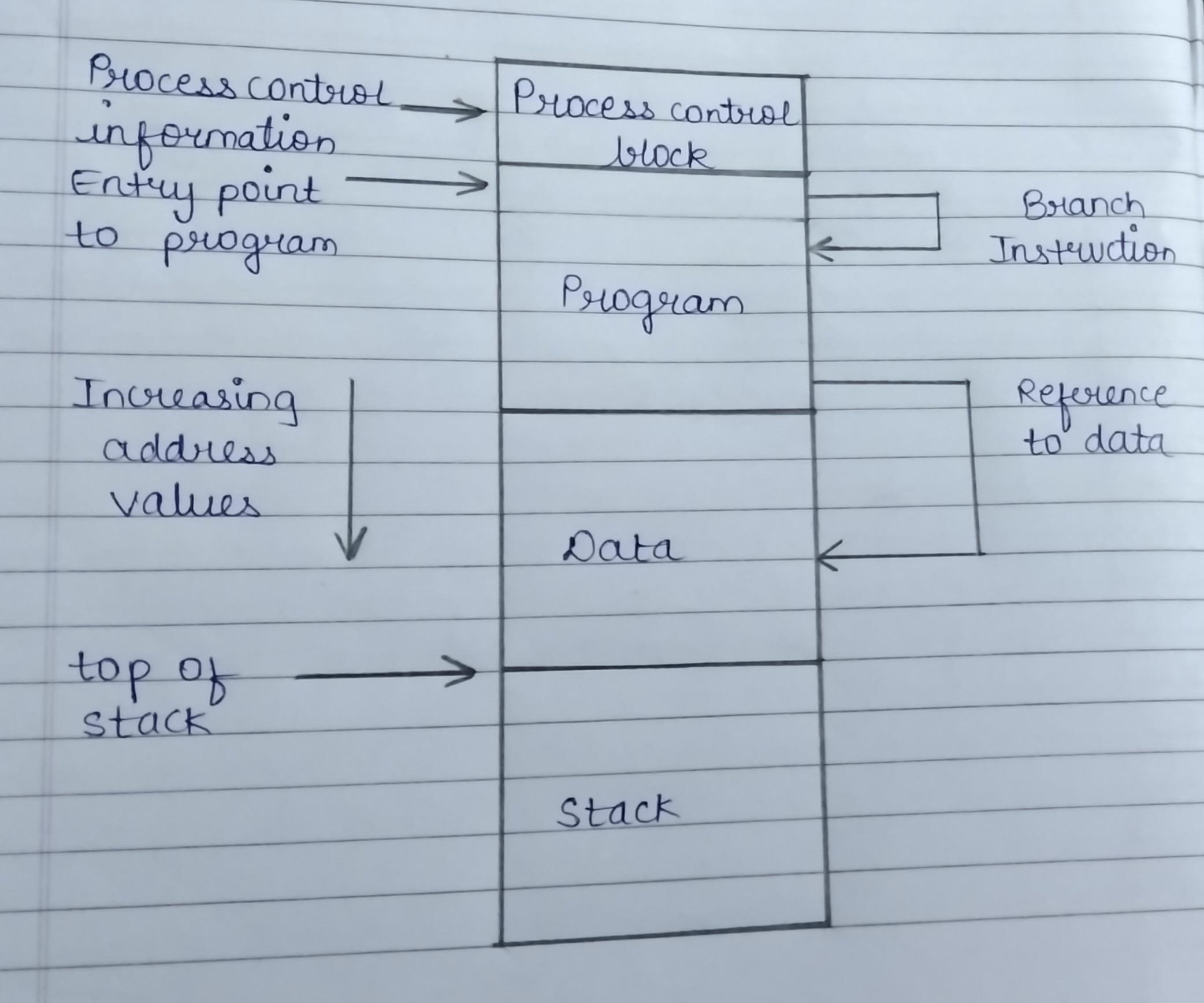
- In a multiprogramming system, memory is shared among multiple processes, making it difficult to predict which programs will be in main memory at the time of execution.
- Swapping active processes allows the operating system to have a larger pool of ready-to-execute processes.
- However, swapping may cause a program to move to a different memory area.
- The operating system needs to know the location of process control information, execution stack, and code entry.
- After loading the program, it must translate logical addresses into physical addresses.
Protection :
- Multiple programs can cause interference, making it crucial to protect processes against unwanted interference.
- A trade-off exists between relocation and protection requirements, as satisfaction of relocation increases protection difficulty.
- Predicting program location in main memory is impossible, so absolute address checks are not possible.
- Memory protection must be satisfied by the processor, as the operating system cannot control processes.
Sharing :
- A protection mechanism must allow multiple processes to access the same main memory portion, allowing controlled access without compromising protection.
- Memory management aims to support relocation-supported sharing capabilities, allowing each process to access the same copy of the program.
Logical organization :
- Main memory is organized as linear or one-dimensional address space, with programs organized into modules.
- These modules can be unmodifiable or modified.
- The operating system and hardware must support a basic module for protection and sharing.
- Advantages include independent writing and compilation, different protection levels, and module-level sharing, allowing user-specified sharing.
Physical organization :
- Computer memory consists of main and secondary memory, with main memory being faster and more costly. Secondary memory is used for long-term data storage, while main memory holds current programs. The main concern is information flow, which can be challenging for programmers due to overlaying and multiprogramming environments, where they cannot predict memory space availability.