


The current cyber security vulnerabilities and countermeasures in smart ship systems. It demonstrated that malicious attacks and incidents with devastating consequences are not only possible, but imminent. The maritime domain leverages cyber technologies to assure the safety and efficiency of operations at sea but vessels, platforms, satellites, and onshore facilities are increasingly interconnected, exposing them to an abundance of systemic and technology based threats.
The outlined the flaws in existing information technology networks on board and concluded that the high level of complexity and shared resources create a wide attack surface which should be segmented and secured systematically. Industrial Control Systems are often built on legacy infrastructure and implemented without security in consideration. Networking capabilities supplement these systems to allow remote control and troubleshooting but at the same time expose them to the IT network and its inherent vulnerabilities.
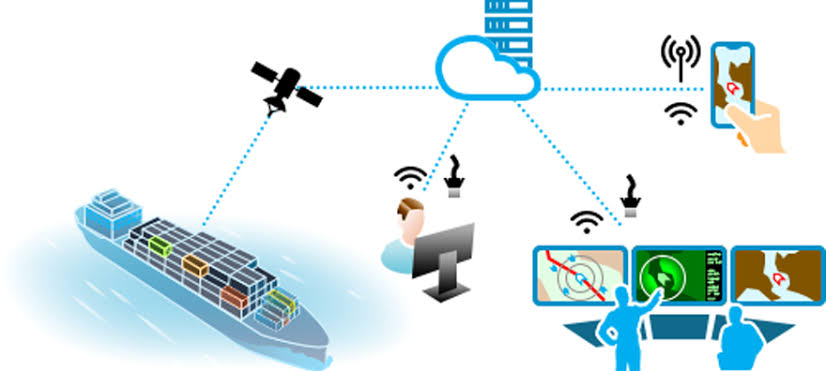
Vessel operators depend on the Automated Identification System for traffic and emergency services. Flaws discovered in the underlying hardware, software, and protocols would allow an adversary to manipulate the transmitted data and this could lead to navigational decisions with devastating outcomes. The Electronic Chart Display Information System equipment is equally unsecure and susceptible to malicious tampering. It often runs on legacy systems with well published vulnerabilities and the software itself can be misused to manipulate maps and sensor data which can compromise the safe navigation at sea.
Very Small Aperture Terminals provide geospatial capabilities for many critical services on board. The data flow between satellites and terminals is unencrypted and provides no integrity checks. Terminals can be tracked over the public internet and many interfaces are not locked down. An attacker could remotely log in to the exposed device and change critical information as well as using it as an entry point to pivot through the connected ship network.
The presented countermeasures were explained in the context of the multi-layered “Defence-in-depth” approach. Further recommendations were based on the implementation of security related policies and procedures.The maritime domain is moving fast towards the paradigm of “smart” transportation with more innovative technologies and AI driven decision-making. While this implies a wealth of benefits for economy, critical infrastructure, and military, it also increases the complexity of the threats to the maritime community before we have discovered and mitigated the flaws in existing systems and legacy technology. The current coverage of research in the field of maritime cyber security is sporadic and fragmented, leaving many stakeholders unaware of the risks and unprepared to treat them.
The cyber security community has the urgent obligation to support the shipping industry with research, tools, security assessments, and education programs. In doing so, we will enable organisations to make informed strategic decisions and effectively allocate resources to protect each member and the maritime community as a whole.Future work based on the present paper will aim to map all identifiable risks and to establish a status quo of the cyber security posture of the maritime sector.