
AUTHOR : Neeta Vonkamuti
Abstract: This research paper will shows what is cyber bullying, the detail types of cyber bullying, how it works and the forms of cyber bullying. This research paper will shows the two tool namely Net Nanny and NuDetective.
Keywords: cyber bullying, internet, messaging.
Introduction:
[1] "Cyberbullying" is when a child, preteen or teen is tormented, threatened, harassed, humiliated, embarrassed or otherwise targeted by another child, preteen or teen using the Internet, interactive and digital technologies or mobile phones. It has to have a minor on both sides, or at least have been instigated by a minor against another minor. Once adults become involved, it is plain and simple cyber- harassment or cyberstalking. Adult cyber-harassment or cyberstalking is NEVER called cyberbullying. It isn't when adult are trying to lure children into offline meetings, that is called sexual exploitation or luring by a sexual predator. But sometimes when a minor starts a cyberbullying campaign it involves sexual predators who are intrigued by the sexual harassment or even ads posted by the cyberbullying offering up the victim for sex. The methods used are limited only by the child's imagination and access to technology. And the cyberbully one moment may become the victim the next. The kids often change roles, going from victim to bully and back again.children have killed each other and committed suicide after having been involved in a cyberbullying. Incident.cyber bullying is usually not a one time communication, unless it involves a death threat or a credible threat of serious bodily harm. Kids usually know it when they see it, while parents may be more worried about the lewd language used by the kids than the hurtful effect of rude and embarrassing posts. Cyberbullying may rise to the level of a misdemeanor cyberharassment charge, or if the child is young enough may result in the charge of juvenile delinquency. Most of the time the cyberbullying does not go that far, although parents often try and pursue criminal charges. It typically can result in a child losing their ISP or IM accounts as a terms of service violation. And in some cases, if hacking or password and identity theft is involved, can be a serious criminal matter under state and federal law. Study session shows how the cyberbullying works and detailed ten forms of cyber bullying. Analysis session shows the Net Nanny tool and NuDetective tool.
Study:
[2] How cyberbullying works?
There are two kinds of cyberbullying, direct attacks (messages sent to your kids directly) and cyberbullying by proxy (using others to help cyberbully the victim, either with or without the accomplice's knowledge). Because cyberbullying by proxy often gets adults involved in the harassment, it is much more dangerous.
[3] A)
Direct Access
- Instant Messaging/Text Messaging Harassment
- Stealing Passwords
- Blogs
- Web Sites
- Sending Pictures through E-mail and Cell Phones
- Internet Polling
- Interactive Gaming
- Sending Malicious Code
- Sending Porn and Other Junk E-Mail and IMs
- Impersonation
- Instant Messaging/Text Messaging Harassment
- a) Kids may send hateful or threatening messages to other kids, without realizing that while not said in real life, unkind or threatening messages are hurtful and very serious. b) Warning wars - Many Internet Service Providers offer a way of "telling on" a user who is saying inappropriate things. Kids often engage in "warning wars" which can lead to kicking someone offline for a period of time. While this should be a security tool, kids sometimes use the Warn button as a game or prank. c) A kid/teen may create a screen name that is very similar to another kid's name. The name may have an additional "i" or one less "e". They may use this name to say inappropriate things to other users while posing as the other person. d) Text wars or text attacks are when kids gang up on the victim, sending thousands of text- messages to the victim's cell phone or other mobile device. The victim is then faced with a huge cell phone bill and angry parents. e) Kids send death threats using IM and text-messaging as well as photos/videos.
- Stealing passwords
- a) A kid may steal another child's password and begin to chat with other people, pretending to be the other kid. He/she may say mean things that offend and anger this person's friends or even strangers. Meanwhile, they won't know it is not really that person they are talking to. b) A kid may also use another kid's password to change his/her profile to include sexual, racist, and inappropriate things that may attract unwanted attention or offend people. c) A kid often steals the password and locks the victim out of their own account. d) Once the password is stolen, hackers may use it to hack into the victim's computer.
- Blogs
Blogs are online journals. They are a fun way for kids and teens to send messages for all of their friends to see. However, kids sometimes use these blogs to damage other kids' reputations or invade their privacy. For example, in one case, a boy posted a bunch of blogs about his breakup with his ex- girlfriend, explaining how she destroyed his life, calling her degrading names. Their mutual friends read about this and criticized her. She was embarrassed and hurt, all because another kid posted mean, private, and false information about her. Sometimes kids set up a blog or profile page pretending to be their victim and saying things designed to humiliate them.
- Web sites
- a) Children used to tease each other in the playground; now they do it on Web sites. Kids sometimes create Web sites that may insult or endanger another child. They create pages specifically designed to insult another kid or group of people. b) Kids also post other kids' personal information and pictures, which put those people at a greater risk of being contacted or found.
- Sending Pictures through E-mail and Cell Phones
- a) There have been cases of teens sending mass e-mails to other users, that include nude or degrading pictures of other teens. Once an e-mail like this is sent, it is passed around to hundreds of other people within hours; there is no way of controlling where it goes. b) Many of the newer cell phones allow kids to send pictures to each other. The kids receive the pictures directly on their phones, and may send it to everyone in their address books. After viewing the picture at a Web site, some kids have actually posted these often pornographic pictures on Kazaa and other programs for anyone to download. c) Kids often take a picture of someone in a locker room, bathroom or dressing room and post it online or send it to others on cell phones.
- Internet Polling
Who's Hot? Who's Not? Who is the biggest slut in the sixth grade? These types of questions run rampant on the Internet polls, all created by yours truly - kids and teens. Such questions are often very offensive to others and are yet another way that kids can "bully" other kids online.
- Interactive Gaming
Many kids today are playing interactive games on gaming devices such as X-Box Live and Sony Play Station 2 Network. These gaming devices allow your child to communicate by chat and live Internet phone with anyone they find themselves matched with in a game online. Sometimes the kids verbally abuse the other kids, using threats and lewd language. Sometimes they take it further, by locking them out of games, passing false rumors about them or hacking into their accounts.
- Sending Malicious Code
Many kids will send viruses, spyware and hacking programs to their victims. They do this to either destroy their computers or spy on their victim. Trojan Horse programs allow the cyberbully to control their victim's computer remote control, and can be used to erase the hard drive of the victim.
- Sending Porn and Other Junk E-Mail and IMs
Often cyberbullies will sign their victims up for e-mailing and IM marketing lists, lots of them, especially to porn sites. When the victim receives thousands of e-mails from pornographers their parents usually get involved, either blaming them (assuming they have been visiting porn sites) or making them change their e-mail or IM address.
- Impersonation
Posing as the victim, the cyberbully can do considerable damage
. They may post a provocative message in a hate group's chatroom posing as the victim, inviting an attack against the victim, often giving the name, address and telephone number of the victim to make the hate group's job easier. They often also send a message to someone posing as the victim, saying hateful or threatening things while masquerading as the victim. They may also alter a message really from the victim, making it appear that they have said nasty things or shared secrets with others.
[4] B)
Cyberbullying by proxy
Cyberbullying by proxy is when a cyberbully gets someone else to do their dirty work. Most of the time they are unwitting accomplices and don't know that they are being used by the cyberbully.
Cyberbullying by proxy is the most dangerous kind of cyberbullying because it often gets adults involved in the harassment and people who don't know they are dealing with a kid or someone they know.
"Warning" or "Notify Wars" are an example of cyberbullying by proxy. Kids click on the warning or notify buttons on their IM screen or e-mail or chat screens, and alert the ISP or service provider that the victim has done something that violates their rules. If the victim receives enough warnings or notifications, they can lose their account. The service providers are aware of this abuse, and often check and see if the warning were justified. But all the cyberbully has to do is make the victim angry enough to say something rude or hateful back. Then, BINGO! they warn them, making it look like the victim had started it. In this case, the ISP or service provider is the innocent accomplice of the cyberbully.
Cyberbullying by proxy sometimes starts with the cyberbully posing as the victim. They may have hacked into their account or stolen their password. They may have set up a new account pretending to be the victim. But however they do it, they are pretending to be the victim and trying to create problems for the victim with the help of others.
The most typical way a cyberbullying by proxy attack occurs is when the cyberbully gets control of the victim's account and sends out hateful or rude messages to everyone on their buddy list pretending to be the victim. They may also change the victim's password so they can't get into their own account. The victim's friends get angry with the victim, thinking they had sent the messages without knowing they have been used by the cyberbully. But it's not always this minor. Sometimes the cyberbully tries to get more people involved.
For example...Mary wants to get Jennifer back for not inviting her to her party. She goes online and, posing as Jennifer, posts "I hate Brittany, she is so stupid, ugly and fat!" on buddyprofile.com. Mary may tell Brittany and her friends that she read the post on buddyprofile.com and blames Jennifer for being mean. Brittany and her friends now start attacking Jennifer, and may report her to buddyprofile.com or her school. They are doing Mary's dirty work for her. Mary looks like the "good guy" and Jennifer may be punished by her parents, lose her account with buddyprofile.com and get into trouble at school. And Brittany and her friends may start to cyberbully Jennifer too.
Sometimes it is much more serious than that. When cyberbullies want to get others to do their dirty work quickly, they often post information about, or pose as, their victim in hate group chat rooms and on their discussion boards. Cyberbullies have even posted this information in child molester chat rooms and discussion boards, advertising their victim for sex. They then sit back and wait for the members of that hate group or child molester group to attack or contact the victim online and, sometimes, offline.
For this to work, the cyberbully needs to post offline or online contact information about the victim. Real information, not the account they used to impersonate the victim (if they are posing as the victim to provoke an attack). For example...Jack is angry that Blake was chosen as captain of the junior varsity basketball team. Blake is black. Jack finds a white supremist group online and posts in their chat room that Blake said nasty things about whites and their group in particular. He then posts Blake's cell phone number and screen name. People from the group start calling and IMing Blake with threats and hateful messages. Jack has no idea how much danger he has placed Blake in, and Blake doesn't know why he in under attack. In cases of cyberbullying by proxy, when hate or child molester groups are involved, the victim is in danger of physical harm and law enforcement must be contacted immediately.
[5] Forms of Cyber Bullying
- Exclusion
- Harassment
- Outing
- Cyberstalking
- Fraping
- Fake Profiles
- Dissing
- Trickery
- Trolling
- Catfishing
- Exclusion
Exclusion is the deliberate act of leaving you out.Exclusion is the deliberate act of leaving someone out. Exclusion can happen in a number of ways:
- The person might be excluded from friends’ parties or
- The person’s friends are having online conversations and tagging other friends but not
- The person isn’t using social networking sites or doesn’t have a smartphone and is deliberately excluded from conversations by others because of this
- Harassment
Harassment is a sustained, constant and intentional form of bullying comprising abusive or threatening messages sent to the person or to a group.This is a very dangerous form of cyberbullying. It can have serious implications for the person’s wellbeing. The messages are generally unkind or malicious, can impact their self-esteem and confidence, and can make them fearful. The constant messaging means that there is no respite from the cyberbully. The cyberbully makes extreme effort to cause fear and pain.
- Outing
Outing is a deliberate act to embarrass or publicly humiliate person or a group through the online posting of sensitive, private or embarrassing information without their consent.Outing can happen in a variety of ways and the information revealed can be serious or trivial. Even reading out the person’s saved messages on their mobile phone can be considered a form of outing. Personal information should not be shared and if someone reveals private information deliberately be sure that the person knows to report it as cyberbullying
- Cyberstalking
This form of cyberbullying can extend to the cyberbully making real threats to the person’s physical wellbeing and/or safety. Cyberstalking can also refer to the practice of adults using the internet to contact and attempt to meet with young people for sexual purposes. It is a very dangerous form of cyberbullying and can have serious consequences if something isn’t done immediately to stop it.
- Fraping
Fraping is when somebody logs into your social networking account and impersonates the person by posting inappropriate content in their name. Fraping is a very serious offence, which many people believe to be funny and entertaining, but it’s not. Impersonating somebody online and ruining their reputation can have serious consequences. Remember Google never forgets so everything rude or otherwise posted online will never be fully gone, even if deleted.
- Fake Profiles
Fake profiles can be created in order for a person to hide their real identity with the intention of cyberbullying the person.The cyberbully might also use someone else’s email or mobile phone to cyberbully them. This would make it appear as if someone else has sent the threats. The cyberbully is afraid in case their identity is revealed, therefore they choose to use fake accounts. This usually means that the cyberbully is someone that your child knows very well, because if they didn’t know them, the perpetrator wouldn’t have to hide their identity.
- Dissing
Dissing is the act of sending or posting cruel information about the person online, to damage their reputation or friendships with others.It can also include posting material online such as photos, screenshots or videos. The cyberbully wants to put a person down, so draws attention to what they are saying about them to make other people think they’re not cool. The cyberbully is usually someone you knows. This can make it really upsetting.
- Trickery
Trickery is the act of gaining your person’s trust so that they reveal secrets or embarrassing information that the cyberbully then shares publicly online.The cyberbully will ‘befriend’ the person and lead them into a false sense of security before breaking their trust and sending their private information to a third party.
- Trolling
Tolling is the deliberate act of provoking a response through the use of insults or bad language on online forums and social networking sites. The troll will personally attack your child and put them down. Their main aim is to make them angry enough to act in the same way. Trolls spend their time looking for vulnerable people to put down. Usually they are looking to make themselves feel good by making others feel bad.
- Catfishing
Catfishing is when another person steals a person’s online identity, usually photos, and re-creates social networking profiles for deceptive purposes.A catfish is someone who wants to hide who they are. They will look at a person’s social networking profile and take any information they want to create a fake persona. Sometimes they will only take the person’s photos and use fake names and information; at other times they could take their name and personal information. It can be hard to understand why a catfish does this but it is important to know that they are potentially damaging.
Analysis:
A) NET NANNY
[7] Net Nanny is a brand of content-control software marketed primarily towards parents as a way to control a child's computer activity. The flagship product allows a computer owner to block and filter Internet content, place time limits on use, and block desktop PC games. [8]

Figure 1: Admin Panel
Net Nanny allows you to set both Admin and Default user settings in the Admin Panel. The Settings allow you to configure Profile, Filtering, Time Controls and Games usability, but also more specific details regarding Family options like Passwords, Exceptions, Reports and Email Notifications.
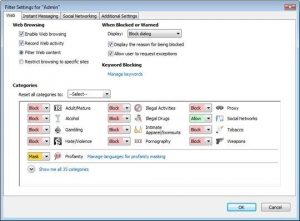
Figure 2: Filter Setting
For the Admin user you can configure the behavior for Web, Instant Message, Social Networking and Additional Settings. You may choose which content categories to block or allow, and whether Web activity should be blocked or not.
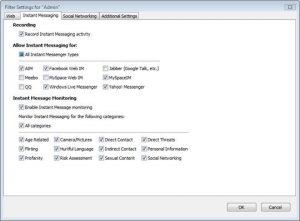
Figure 3: Instant Messaging
Also from the Admin Panel you can configure and monitor particular things for Instant Messaging, like allowing which software to be used for chat and what content categories to be monitored.
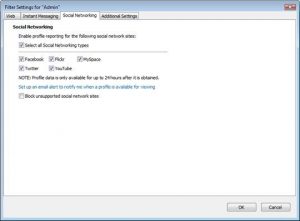
Figure 4: Social Network
An important feature for common security attacks is the Social Networking monitoring option, which you can enable from here. This allows you to enable or disable access to specific sites and allow profile data reporting.
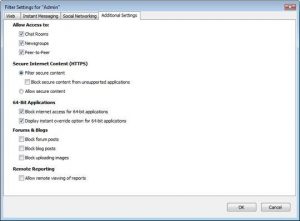
Figure 5: Additonal setting
From the Admin Panel you can control access to chat rooms, newsgroups or peer-to-peer sites, but also to https sites, 64-bit applications and blog or forum posting.
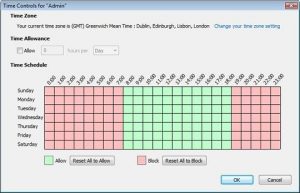
Figure 6: Time Zone
This feature allows you to control the timeframes in which internet access is allowed, according to your time zone. You may also set a certain daily amount of time for internet allowance.
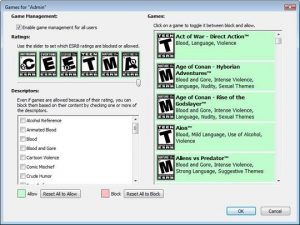 Figure 7: Game Zone
Figure 7: Game Zone
For gaming management you can block or allow any of the installed games on your machine, either by their names or by their ratings. You may easily block all access to games with a single click.
[9] Net Nanny boasts excellent ease of use, with quickly accessible documentation and the ability to search support topics by keyword. Its anti-cyberbullying capabilities, combined with social network monitoring, chat monitoring and time management, give you the greatest number of tools to control the kid's online activities. Activity recording features are far reaching, and reporting and notification features give you an orderly way of reviewing all information gathered. Help and support channels are plentiful and offer the greatest level of coverage available.
B) NUDETECTIVE, THE FORENSIC TOOL
[6] Developed with the
Java Standard Edition (JSE) by forensic experts of Brazilian Federal Police, the NuDetective Forensic Tool implements the proposed approach and many other options that can be configured by the forensic examiner to assist in the detection of child pornography files.
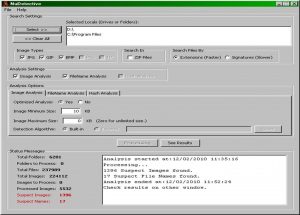 Figure 8: main GUI of NuDetective Forensic Tool
Figure 8: main GUI of NuDetective Forensic Tool
First, the forensic examiner chooses
locations to search, such as folders and/or disk partitions, and configures search options. The NuDetective then scans all files from selected
locations searching for images and submitting them to the nudity analysis process called
Image Analysis. In addition, the Tool can still check the names of all files or only images name, comparing them with a list of pre-defined keywords1 that contains names and phrases commonly used to share child pornographic files over the Internet. The
File Name Analysis allows finding other types of suspicious files, such as videos, for example, that are not verified by
Image Analysis process. Several options can be configured by the forensic examiner, such as the image types to be searched, the method to search for images (by file extensions or by file signatures), filters by image sizes, how to compare names on File Name Analysis, among others. The Tool also allows the analysis of compressed files in ZIP format. The NuDetective Forensic Tool was developed with the primary purpose to assist the forensic examiner to conduct searches for child pornography files at crime scenes, but may also be utilized in a forensic laboratory. Therefore, the use of the Tool should bring quick and efficient results, allowing the analysis of digital storage devices to be done in a short period of time. Thus, the Tool was implemented using threads, allowing the execution of some tasks in parallel.
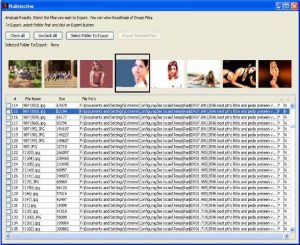
Figure 9: results GUI of NuDetective Forensic Tool.
One of the developed threads is responsible for searching the selected
locations, the second aims only at the nudity images processing and a third thread is responsible for displaying the results on the GUI, illustrated in
Figure 9, in real time. The results GUI also provides the forensic examiner the ability to select and export the suspicious files to a desirable folder or also "launch" the files to the operating system in order to be displayed by their native programs. The Tool can be easily configured to display texts in Brazilian Portuguese and English languages. New languages can be added in the future without the need for a new implementation.
Conclusion:
If a person face the cyber bullying problem should simply avoid that person. Either way a person can simply block that person. Remember to take evidence with them like screenshot of the online image or the copy of the messages communication Report them on social media respectively. If there is no response from social media sites then person have force them to take actions. Should be aware of what data information to be provide online. Discuss the issues with their parents or an adult.
Future Enhancement:
Once information shared online stays online forever. In the Net Nanny tool social networking monitor is somewhat limited and only one license needed.
References:
[1]
http://www.stopcyberbullying.org/what_is_cyberbullying_exactly.html
[2]
http://www.stopcyberbullying.org/how_it_works/index.html
[3]
http://www.stopcyberbullying.org/how_it_works/direct_attacks.html
[4]
http://www.stopcyberbullying.org/how_it_works/cyberbullying_by_proxy.html
[5] https://kids.kaspersky.com/10-forms-of-cyberbullying/
[6]
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=5591120&isnumber=5590741
M.d. Castro and P. M. da Silva Eleuterio, "NuDetective: A Forensic Tool to Help Combat Child Pornography through Automatic Nudity Detection,"
2010 Workshops on Database and Expert Systems Applications, Bilbao, 2010, pp. 349-353.
[7] https://en.wikipedia.org/wiki/Net_Nanny
[8]
http://www.comparedandreviewed.com/parental-control-software/net- nanny/screenshots#screenshots
[9]
http://www.toptenreviews.com/software/security/best-internet-filter-software/netnanny-review/










 Figure 7: Game Zone
Figure 7: Game Zone Figure 8: main GUI of NuDetective Forensic Tool
Figure 8: main GUI of NuDetective Forensic Tool