


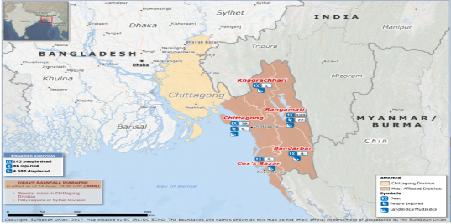
Around 700.000 Rohingya refugees have crossed the border between Mynamar and Bangladesh and live in refugee camps in the landslide exposed areas in eastern part of Bangladesh. With support from the Ministry of The Norwegian Foreign Affairs, NGI did mapping and installed many avalanche warning systems between 2009-12. These systems can predict rainfall induced landslides, and have thereby saved many lives in landslide prone areas. The United Nations Office in Bangladesh is now looking to expand these systems for enhanced landslide management. All of this wouldn’t have been possible without GIS services, which has made such advancements a reality.