


In operating systems, starvation (or indefinite blocking) refers to a situation where a process is perpetually denied access to resources it needs to make progress, even though the resources are available. This typically happens in systems that use scheduling algorithms for resource allocation.
Causes of Starvation:
1. Priority Scheduling: If a scheduling algorithm always favors higher-priority processes, lower-priority processes might be starved of CPU time.
2. Resource Allocation: When a process holds resources while waiting for others, and other processes keep grabbing the resources it needs, the process can end up waiting indefinitely.
3. Long Wait Queue: In some scheduling systems, processes at the end of the queue might never get a chance to execute if new processes keep arriving and getting added to the front of the queue.
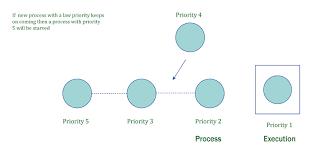
Example:
Consider a system using a priority-based scheduling algorithm where high-priority processes are always chosen over low-priority ones. If high-priority processes keep entering the system, a low-priority process may never get CPU time, leading to starvation.
Solutions to Starvation:
1. Aging: Gradually increasing the priority of a waiting process over time, ensuring that it eventually gets scheduled.
2. Fair Resource Allocation: Ensuring that every process gets a fair share of resources, perhaps by implementing round-robin or time-sharing scheduling.
3. Deadlock Detection: vIdentifying potential deadlocks and resolving them, as deadlocks can lead to starvation in some cases.
Starvation is a significant issue in operating systems and resource management algorithms, as it can lead to inefficiency and poor system performance.