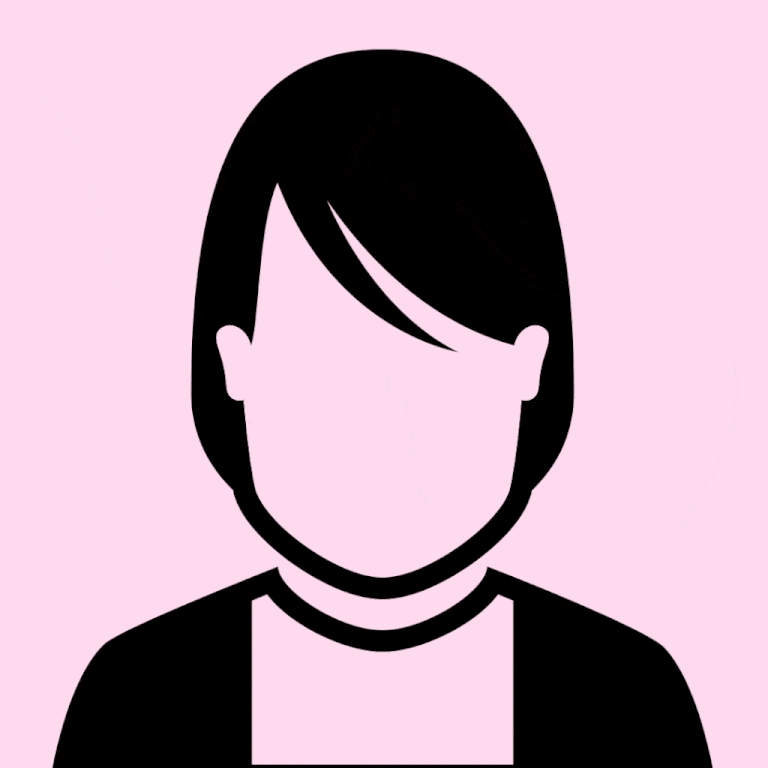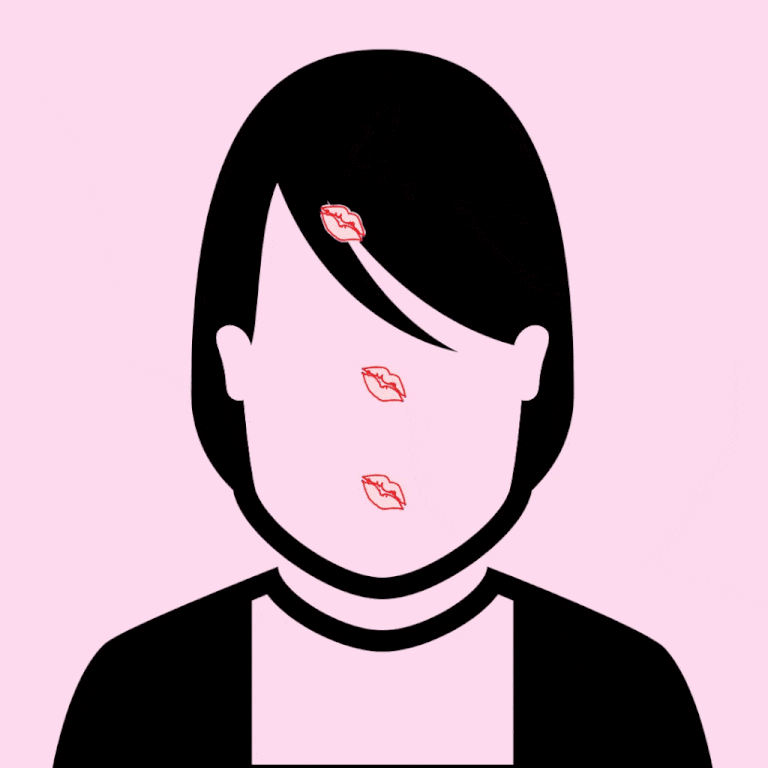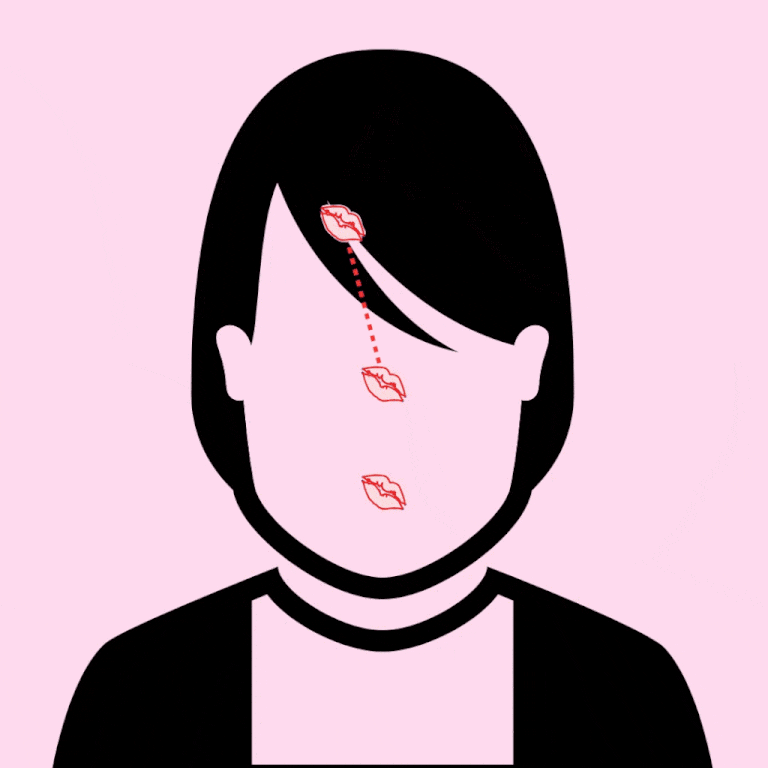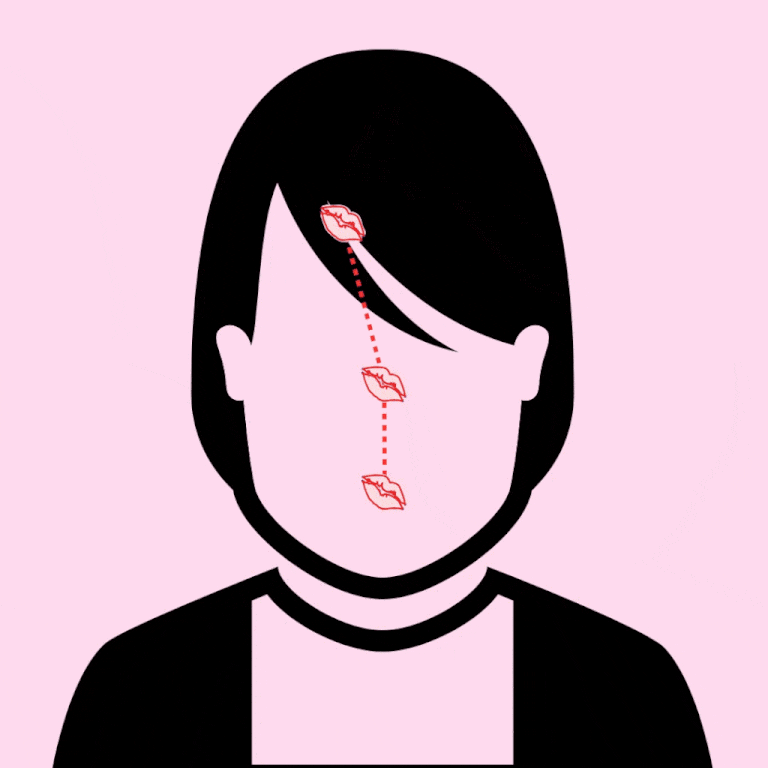
Found this on the internet and was amazing so thought of sharing
Consider this a google map like guide to kissing:
1. START AT THE LIPS, KISSING (NO TONGUE) GENTLY DOWN TOWARDS THE CHIN, THEN ALL ALONG THE JAWBONE, TOWARDS THE EAR. FROM HERE, GIVE THEIR EARLOBE A LITTLE NIP, OR WHISPER SOFTLY … "SO WHEN ARE WE GETTING CHIPOTLE?" (OPTIONAL.)
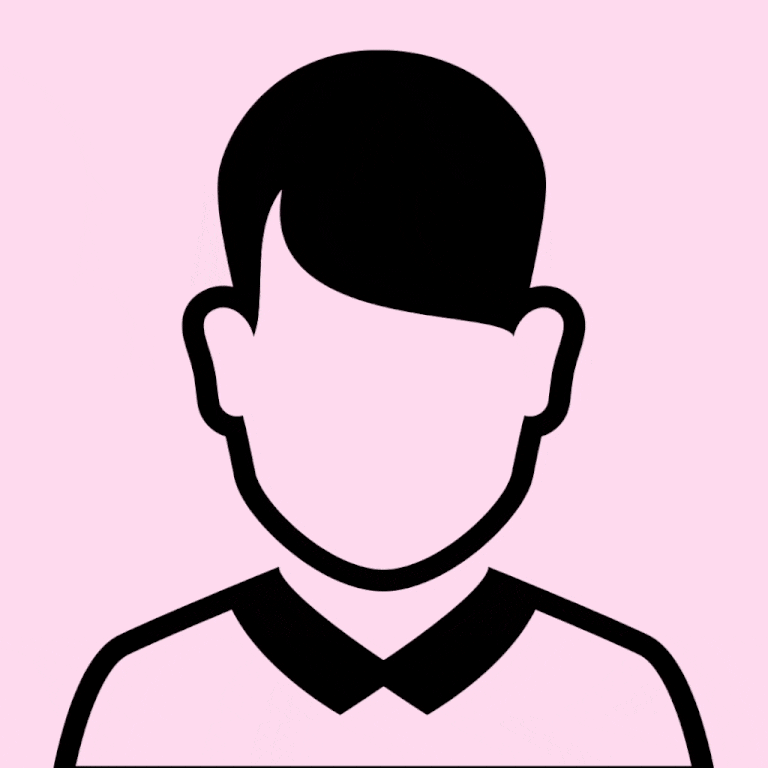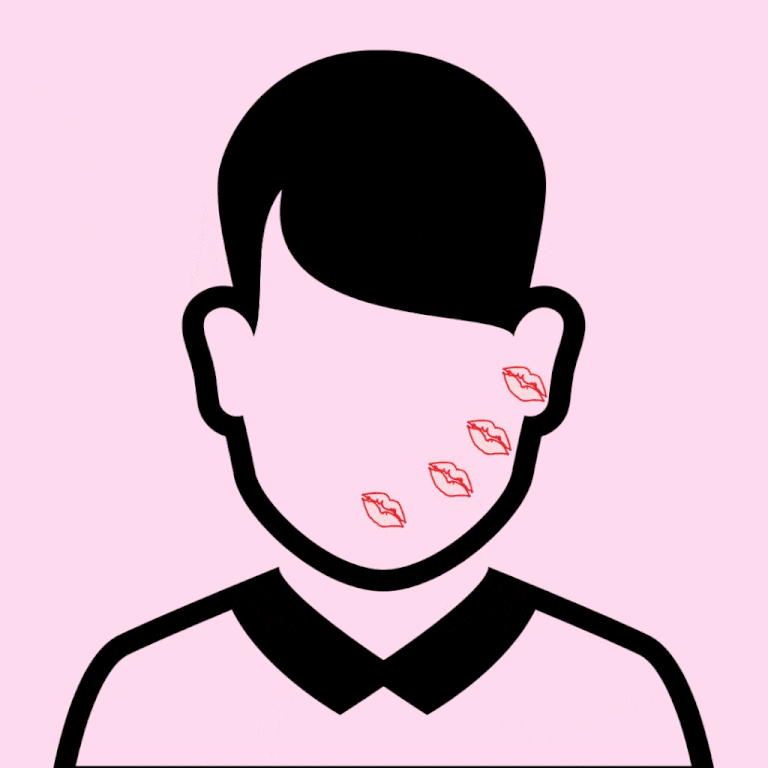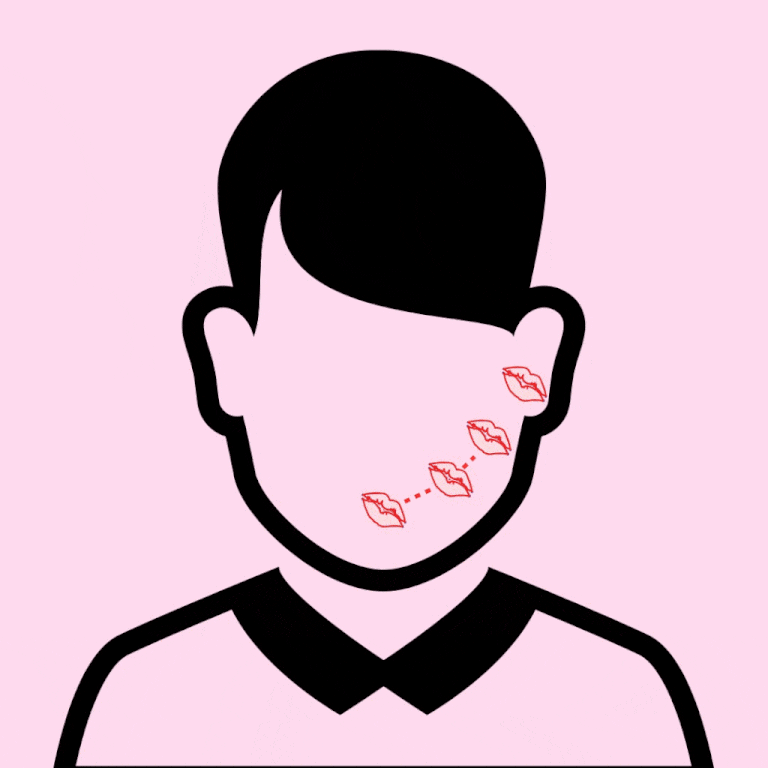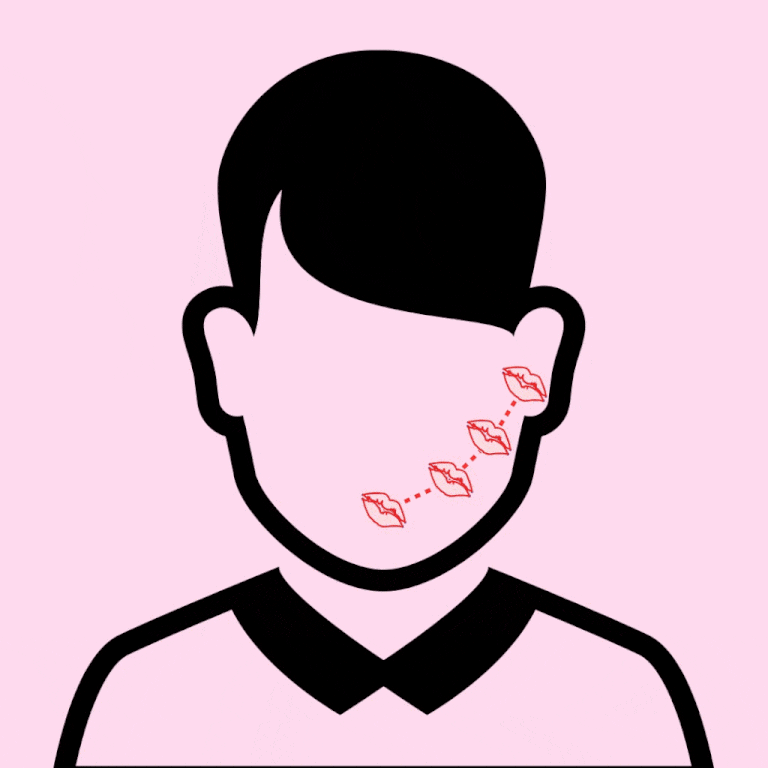
2. SNEAK UP ON BAE FROM BEHIND AND KISS FROM THE TOP OF THEIR SHOULDER, ALONG THE CURVE TOWARDS THEIR EAR. (AND AGAIN, THE OPTIONAL WHISPER: "I WANT TO EAT AN ENTIRE PIZZA WITH YOU.")
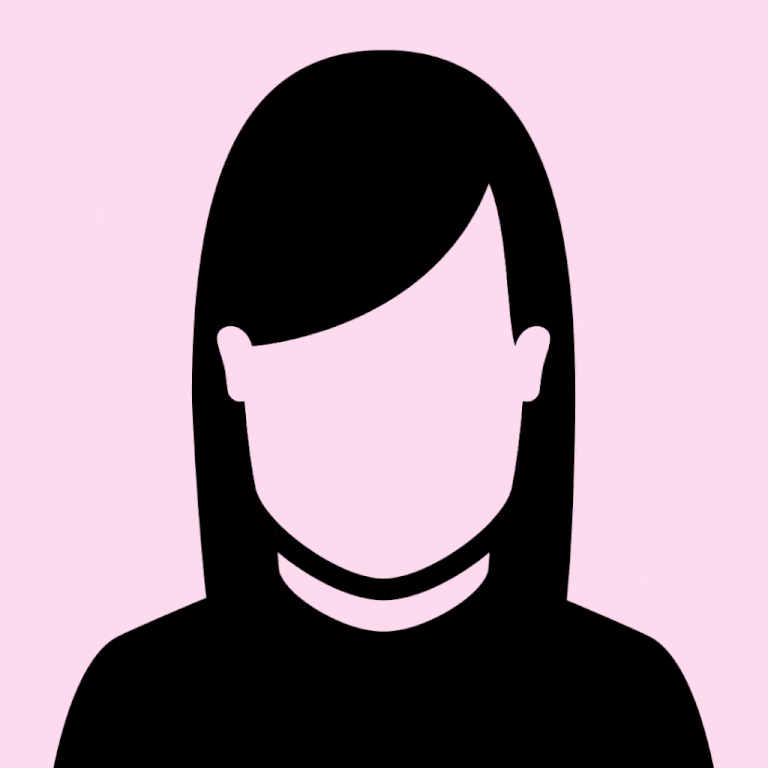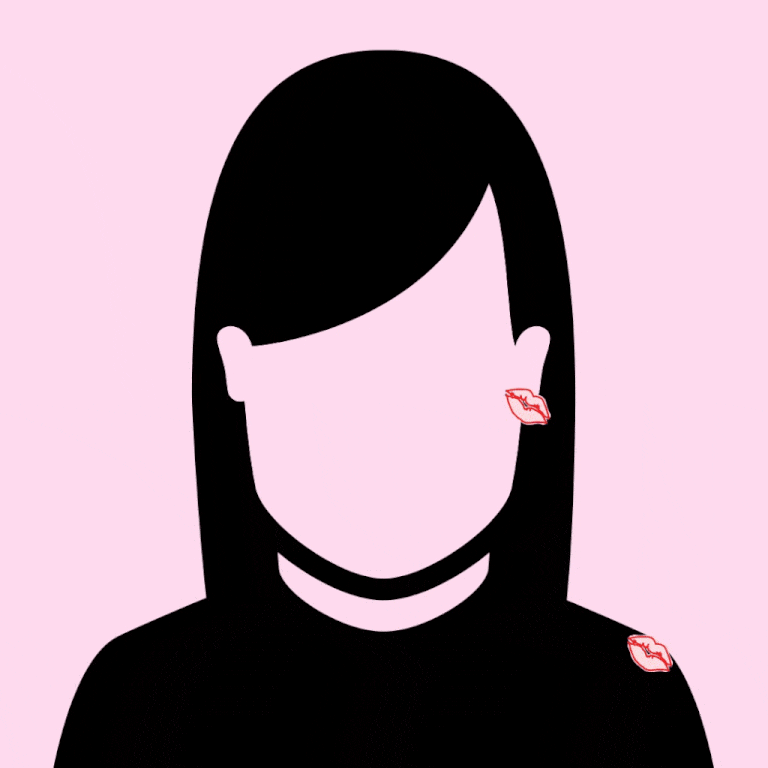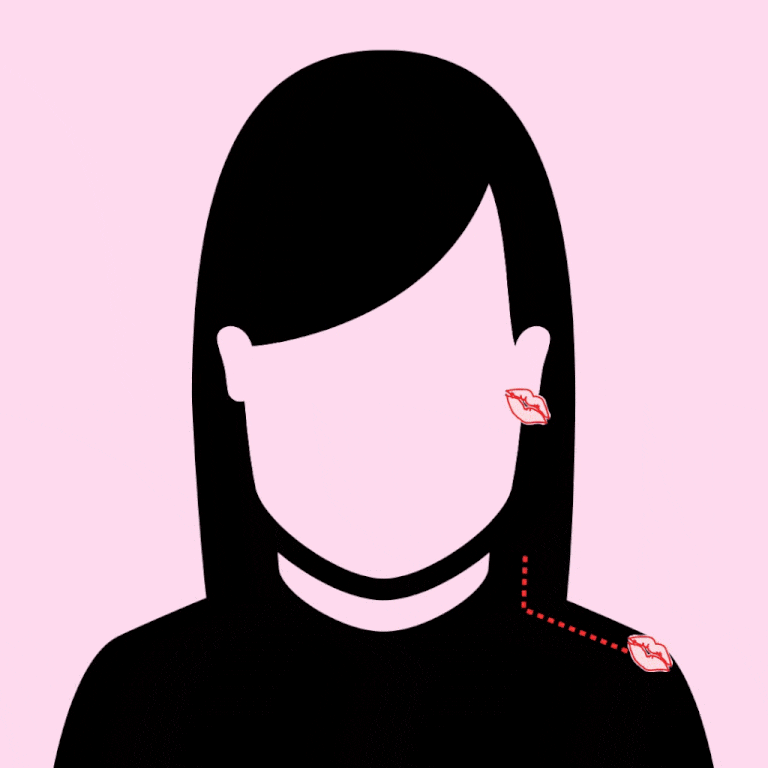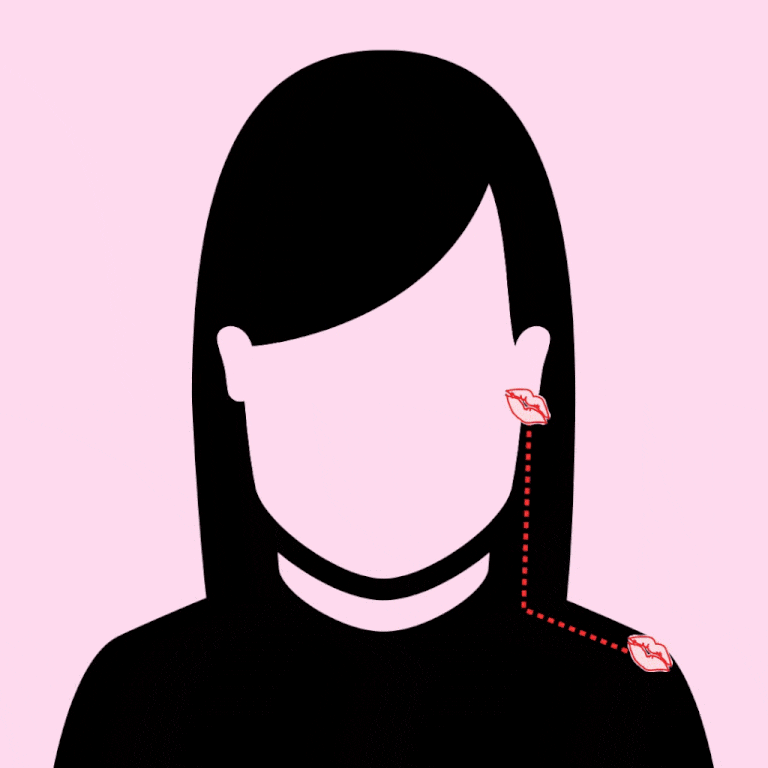
3. GENTLY KISS DOWN THE FOREHEAD, STARTING AT THE HAIRLINE, ALONG THE SLOPE OF THE NOSE, ENDING AT THE LIPS. CONGRATS: YOU'RE NOW SO *GODDAMN CUTE.*