


Logical And Physical Addresses
An address generated by the CPU is commonly refereed as Logical Address, whereas the
address seen by the memory unit that is one loaded into the memory address register of the
memory is commonly refereed as the Physical Address. The compile time and load time
address binding generates the identical logical and physical addresses. However, the
execution time addresses binding scheme results in differing logical and physical addresses.
The set of all logical addresses generated by a program is known as Logical Address Space,
where as the set of all physical addresses corresponding to these logical addresses is
The user program never sees the real physical address space, it always deals
with the Logical addresses. As we have two different type of addresses Logical address
in the range (0 to max) and Physical addresses in the range(R to R+max) where R is
the value of relocation register. The user generates only logical addresses and thinks that
the process runs in location to 0 to max. As it is clear from the above text that user program
supplies only logical addresses, these logical addresses must be mapped to physical address
before they are used.
Base and Limit Registers
A pair of base and limit registers define the logical address space
Physical Address Space. Now, the run time mapping from virtual address to physical
address is done by a hardware device known as Memory Management Unit. Here in the
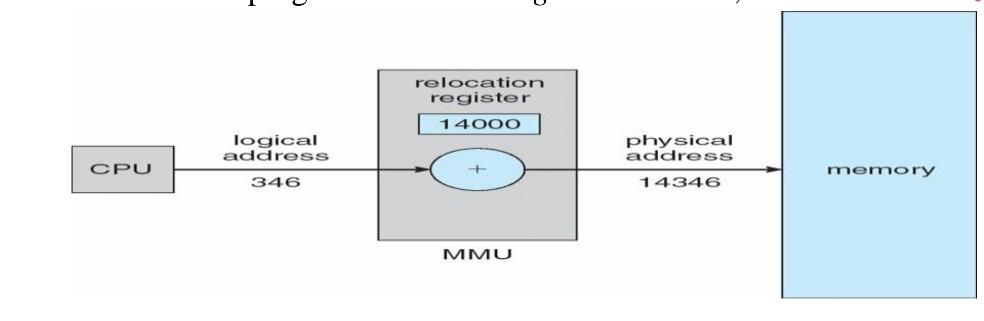
case of mapping the base register is known as relocation register. The value in the relocation
register is added to the address generated by a user process at the time it is sent to memory
.Let's understand this situation with the help of example: If the base register contains the
value 1000,then an attempt by the user to address location 0 is dynamically relocated to
location 1000,an access to location 346 is mapped to location 1346.
Memory-Management Unit (MMU)
Hardware device that maps virtual to physical address
In MMU scheme, the value in the relocation register is added to every address generated by a user
process at the time it is sent to memory
The user program deals with logical addresses; it never sees the real physical addresses