


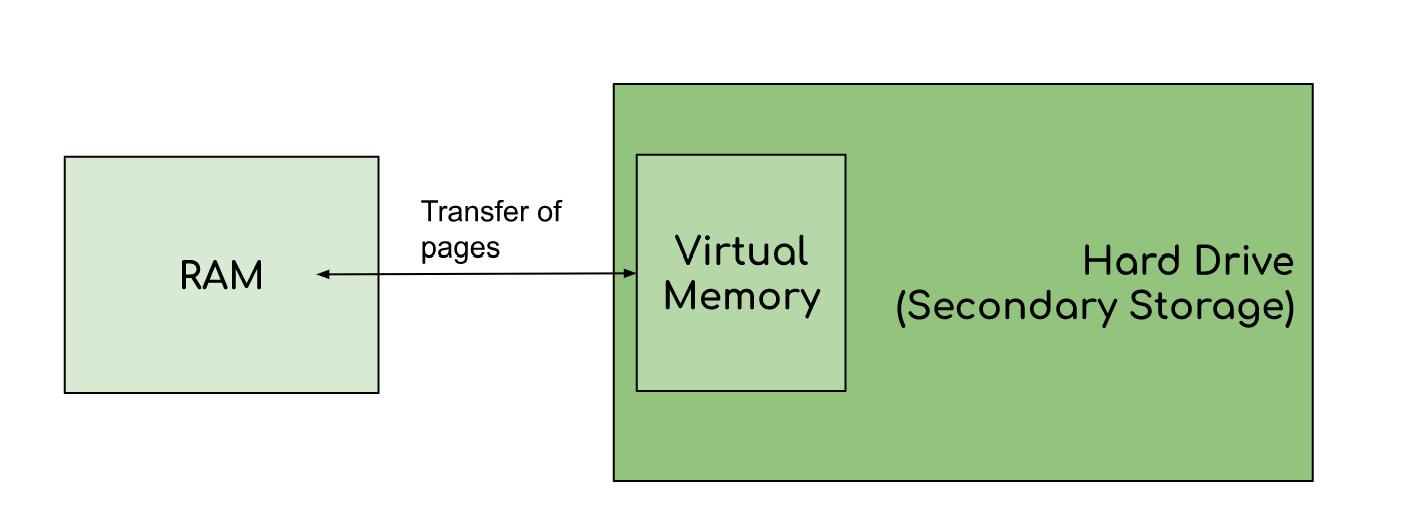
Virtual memory in operating system is defined as technique of management of memory where main memory can be stored in secondary memory as if it is a part of it. So let us understand why is it called virtual memory? A memory management which provides an idealized representation of the storage resources available on a machine, creating the illusion for users of having a very large main memory. It is the space of HDD or SSD that acts as a part of system's RAM(Random Access Memory). Virtual Memory or Virtual Storage is enacted using "demand paging". A page is only loaded into memory when it is specifically referenced. Now let's grasp some knowledge about how virtual storage is operated. The operating system splits memory with a set number of addresses into pagefiles or swap files. The optimistic advantage of virtual memory are as follows:-
1.Large Memory:-Virtual memory gives more storage area as compared to physically present in the system by utilizing disk space as an extension of physical RAM.
2.Memory paging:- It divides memory into fixed-size blocks called pages so that day is allocated in an organized way
3.Demand Paging: An optimization technique used with virtual memory where pages are loaded into RAM only when they are needed, rather than loading the entire program into memory at once. There are many advantages of it but as a coin has two sides there are some flaws also of it. Some of the disadvantages of Virtual Memory are as follows:-
Neha mendapara
53003230074
Div A