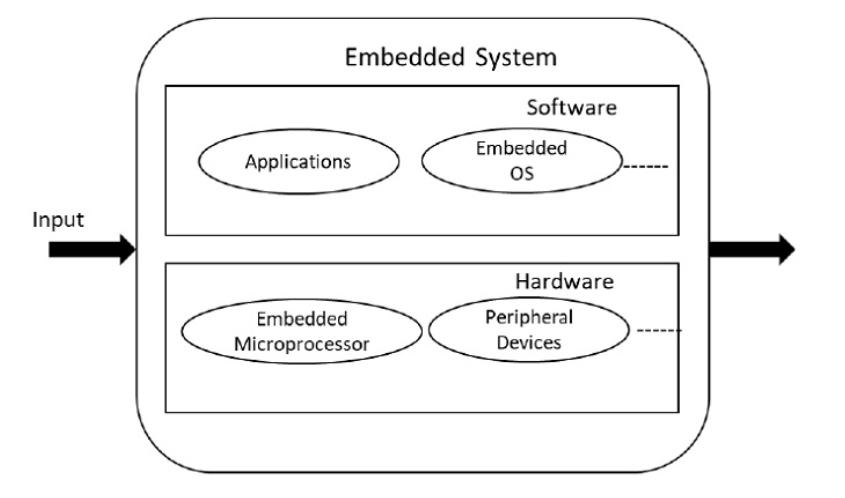
Embedded Operating system
All Embedded Systems are task specific. They mostly do a particular task on loop/repeatedly for their entire lifetime. These systems are designed to execute their task within a particular time interval, and thus they have to be fast enough to be up to their time limit.
They have little or no user interface like a fully automatic washing machine does its task fully once its programmed is set and stops after its work is finished with almost no user interface.
They are built to achieve a particularly good efficiency level. They are very small in size operating system, need little power
These systems can't at all be upgraded or updated. Thus, they must be really high on efficiency and reliability as they can't be updated.
Advantages
The advantages of embedded operating system are as follows −
- Portable
- Much faster than other operating systems
- Less Hardware requirement
- Highly Predictable
Disadvantages
The disadvantages of embedded operating system are as follows −
- Less optimization
- High modification is required
- Customization is time taking process
Characteristics
The characteristics of the embedded operating systems are as follows −
- All Embedded Systems are task specific. They mostly do a particular task on loop/repeatedly for their entire lifetime.
- All embedded systems are designed to execute their task within a particular time interval, and thus they have to be fast enough to be up to their time limit.
- They have little or no user interface like a fully automatic washing machine does its task fully once its programmed is set and stops after its work is finished with almost no user interface.
- They are built to achieve a particularly good efficiency level. They are very small in size and, need little power.
- These systems can't at all be upgraded or updated. Thus, they must be really high on efficiency and reliability as they can't be updated.
Roles
The roles performed by embedded operating system are as follows −
Resource allocator
- The role of a resource allocator is to act as a manager. The basic task is to manage the resources of both the hardware and software to allocate and assign them to the specific program and user. It helps in the proper use of the OS and also supports the better execution of the programs.
Resource controller
- The role of the resource controller is to help the programmer and the system manager in the creation and the controlling of the subsystem. This task is accomplished with the help of a certain set of commands and subroutines.
Resource monitor
- The role of the Resource monitor is to act as a utility in the Windows Operating System to let the user monitor the use of the hardware that is, CPU, memory, disk, and network along with the software that is various file handles and modules. This task is done in real-time and the performance of the OS is improved and utilized as per the requirement.
User-friendly interface
- The User interface, usually termed as UI is the medium with the help of which a user or person interacts with the hardware or the software to get his required task complete.
- Now, the interface which is designed in such a manner that it does not confuse the user and the user can easily interact with the system is called a User-friendly interface.
- If the User interface of a given software or hardware is User-friendly then it gains trust and the confidence of the user increases respectively. It is more demanded over a normal interface.